Windows Alert: Critical SMB_v3 Flaw Requires Workaround
Data Breach Today
MARCH 11, 2020
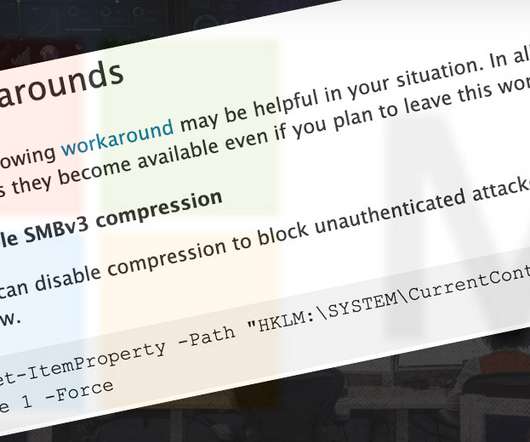
Microsoft Recommends Emergency Disabling of SMBv3 Compression, Pending Patches Microsoft has confirmed that a serious flaw in Windows SMB_v3 exists that could be exploited by attackers to remotely seize control of vulnerable systems. While no attacks have been seen in the wild, no patch for the wormable flaw is yet available. A workaround exists for servers, but not clients.




































Let's personalize your content