PwndLocker: Free Decryptor Frees Crypto-Locked Data
Data Breach Today
MARCH 10, 2020
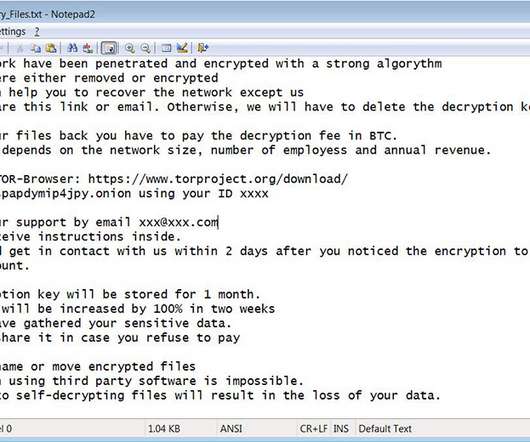
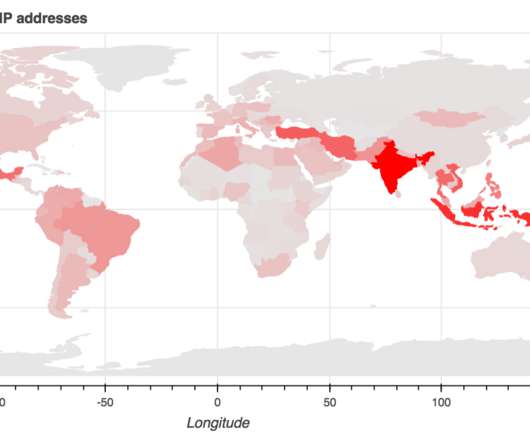
Ransomware Debuted in Late 2019; Gang's Ransom Demands Have Hit $660,000 in Bitcoins Security firm Emsisoft is offering free, customized decryptors to victims of PwndLocker ransomware, which first surfaced in late 2019 and has been tied to attacks against Lasalle County in Illinois and the Serbian city of Novi Sad, with the gang demanding up to $660,000 or more in bitcoins from its victims.





































Let's personalize your content