Hackers Posing as Ukrainian Ministry Deploy Info Stealers
Data Breach Today
FEBRUARY 3, 2023
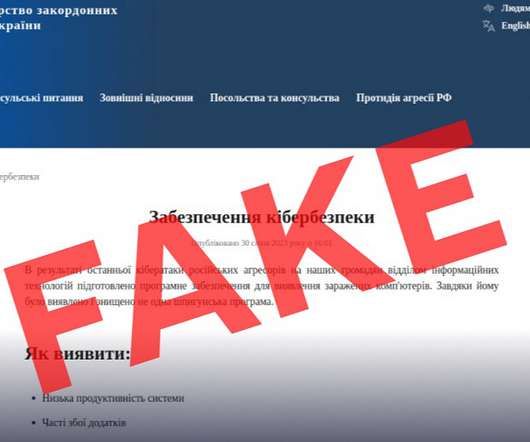
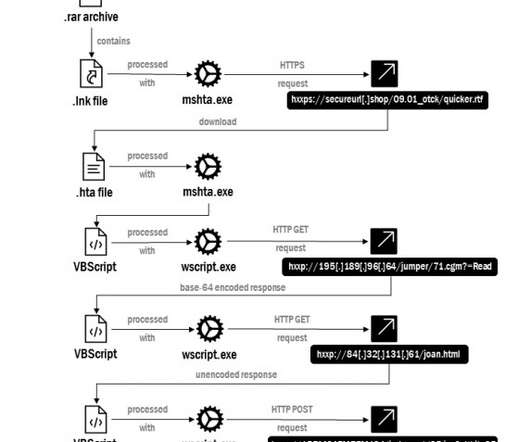
Spoofed Polish Police Websites Also Found Ukrainian and Polish cyber defenders are warning against a slew of phishing websites that mimic official sites, in particular a page that mimics the Ministry of Foreign Affairs of Ukraine. A hacking group likely comprised of Russian speakers uses the pages to lure users into downloading software.








































Let's personalize your content