Hacker Charged With Extorting Online Psychotherapy Service
Krebs on Security
NOVEMBER 3, 2022
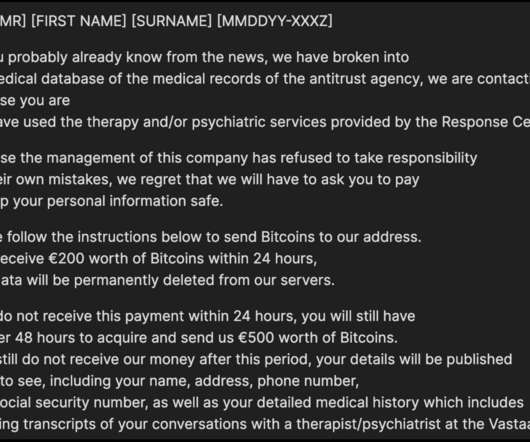
A 25-year-old Finnish man has been charged with extorting a once popular and now-bankrupt online psychotherapy company and its patients. Finnish authorities rarely name suspects in an investigation, but they were willing to make an exception for Julius “Zeekill” Kivimaki , a notorious hacker who — at the tender age of 17 — had been convicted of more than 50,000 cybercrimes , including data breaches, payment fraud, operating botnets, and calling in bomb threats.





































Let's personalize your content