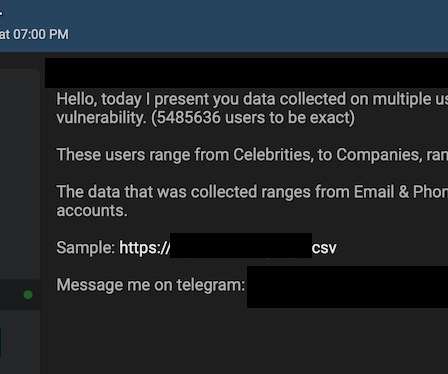
A database containing data of 5.4 million Twitter accounts available for sale
Security Affairs
JULY 24, 2022
Threat actor leaked data of 5.4 million Twitter users that were obtained by exploiting a now patched flaw in the popular platform. A threat actor has leaked data of 5.4 million Twitter accounts that were obtained by exploiting a now-fixed vulnerability in the popular social media platform. The threat actor is now offering for sale the stolen data on a the popular hacking forum Breached Forums.











Let's personalize your content