Phishing Campaign Targets QuickBooks Users
KnowBe4
JUNE 1, 2022
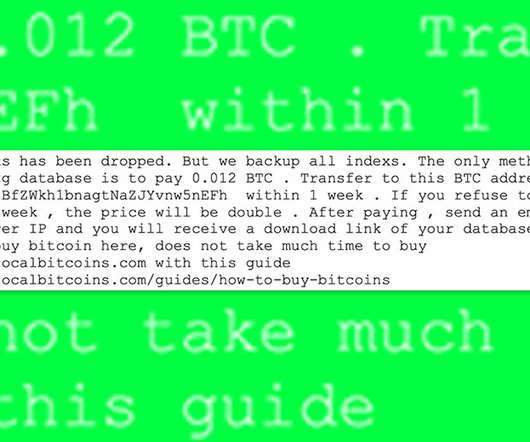
Accounting software provider Intuit has warned of a phishing scam targeting its customers, BleepingComputer reports. The phishing campaign affected users of Intuit’s QuickBooks product, informing them that their account has been put on hold.




































Let's personalize your content