Wanted: Disgruntled Employees to Deploy Ransomware
Krebs on Security
AUGUST 19, 2021
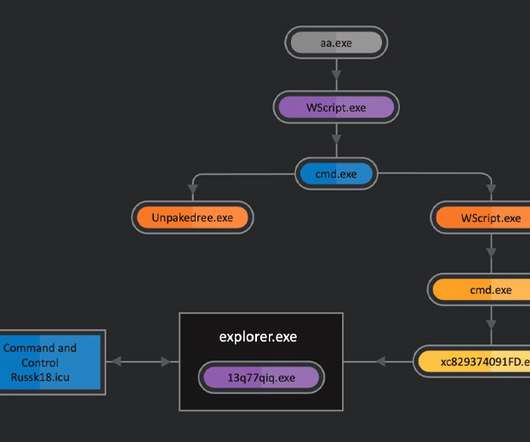
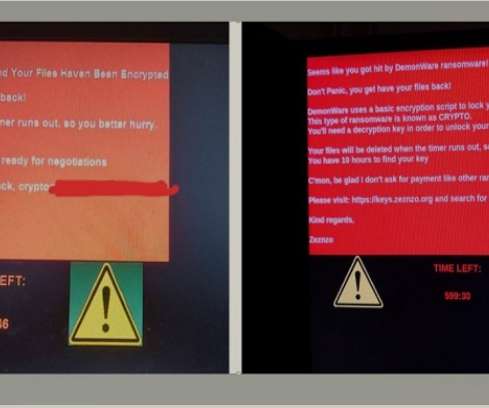
Criminal hackers will try almost anything to get inside a profitable enterprise and secure a million-dollar payday from a ransomware infection. Apparently now that includes emailing employees directly and asking them to unleash the malware inside their employer’s network in exchange for a percentage of any ransom amount paid by the victim company.








































Let's personalize your content