Pandemic Threat Reality
Daymark
SEPTEMBER 30, 2020
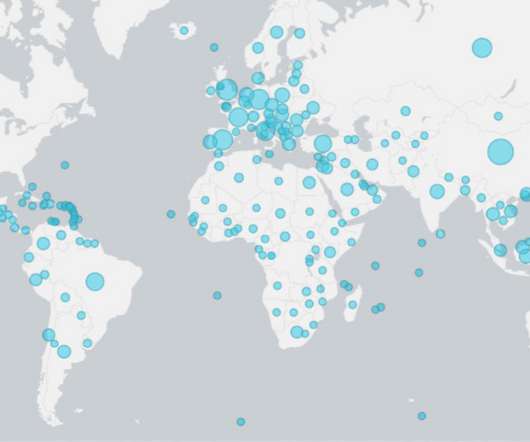
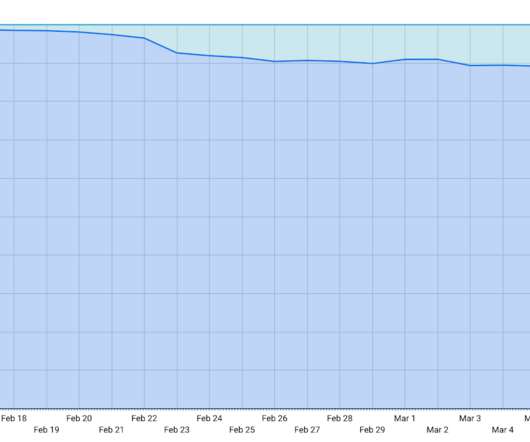
Mimecast held their 2020 Cyber Resilience Summit remotely this year covering a wide range of topics. You can read our previous blog “ Mimecast Cyber Resilience Summit 2020 – Key Takeaways ” for those highlights. In addition, Mimecast provided some alarming data on the pandemic threat reality that we are facing. Mimecast collected 100 days of detection data from January 2020 to April 2020.





































Let's personalize your content