German Parliament Sustains Another Attack
Data Breach Today
MARCH 27, 2021
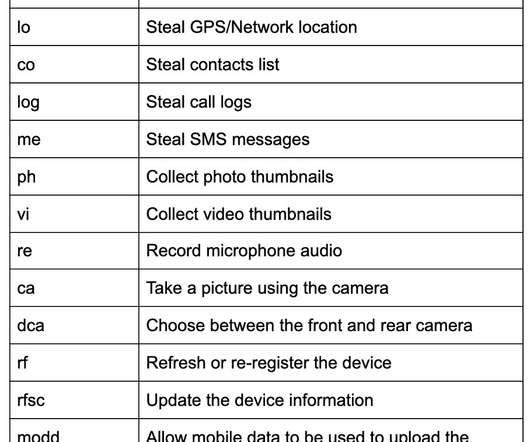
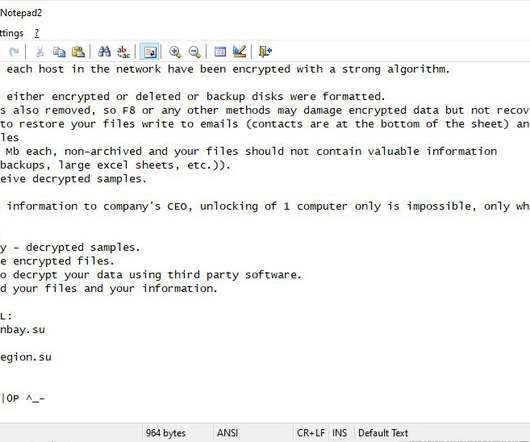
Members of Parliament Targeted by Spear Phishing, German Media Reports Several members of the German parliament, The Bundestag, and political activists in the country were targeted using a spear-phishing campaign, German newsmagazine der Spiegel reported Friday. This is second such incident, following the 2015 parliament hack.














Let's personalize your content