New Attack Uses Fake Icon To Deliver Trojan
Data Breach Today
MARCH 13, 2021
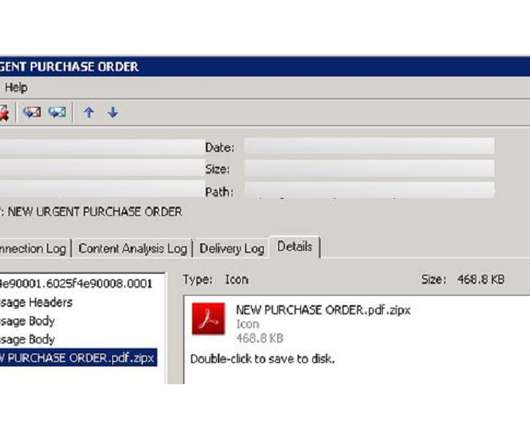
Attackers Deploy NanoCore Malware as Part of the Campaign A new malware spam email campaign is delivering the NanoCore remote access Trojan as a malicious Adobe icon to infect its victims, a new report by security firm Trustwave finds. The malware is designed to steal information from PCs such as passwords and emails.















Let's personalize your content