Proton Is Trying to Become Google—Without Your Data
WIRED Threat Level
MAY 25, 2022
The encrypted-email company, popular with security-conscious users, has a plan to go mainstream.

WIRED Threat Level
MAY 25, 2022
The encrypted-email company, popular with security-conscious users, has a plan to go mainstream.

Data Breach Today
MAY 25, 2022
An effort to establish industry benchmarks for medical device cybersecurity maturity aims to help advance overall cybersecurity in the healthcare sector, says Rob Suárez, CISO of medical device maker Becton, Dickinson and Co. He discusses how to improve the state of medical device cybersecurity.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Affairs
MAY 25, 2022
US Critical Infrastructure Security Agency (CISA) adds 41 new vulnerabilities to its Known Exploited Vulnerabilities Catalog. The Cybersecurity & Infrastructure Security Agency (CISA) has added 41 flaws to its Known Exploited Vulnerabilities Catalog, including recently addressed issues in the Android kernel ( CVE-2021-1048 and CVE-2021-0920) and Cisco IOS XR ( CVE-2022-20821 ).

Data Breach Today
MAY 25, 2022
Cribl Plans to Develop Hosted Versions of the Company's On-Premises Technology Cribl has raised $150 million to drive the development of new features such as hosted versions of the company's technology. The company will build out separate tools for each piece of the observability process rather than forcing customers to purchase a bundle with features they don't care about.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.

Security Affairs
MAY 25, 2022
Security flaws in Zoom can be exploited to compromise another user over chat by sending specially crafted messages. A set of four security flaws in the popular video conferencing service Zoom could be exploited to compromise another user over chat by sending specially crafted Extensible Messaging and Presence Protocol ( XMPP ) messages. Tracked from CVE-2022-22784 through CVE-2022-22787, the issues range between 5.9 and 8.1 in severity.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

Schneier on Security
MAY 25, 2022
Yet another adversarial ML attack: Most deep neural networks are trained by stochastic gradient descent. Now “stochastic” is a fancy Greek word for “random”; it means that the training data are fed into the model in random order. So what happens if the bad guys can cause the order to be not random? You guessed it— all bets are off. Suppose for example a company or a country wanted to have a credit-scoring system that’s secretly sexist, but still be able to pretend that its training was act

Data Breach Today
MAY 25, 2022
Mend Is Pushing Beyond SCA to Safeguard First-Party Code and Automate Remediation WhiteSource has renamed itself Mend as the company pushes beyond software composition analysis to become a broad application security platform with automated remediation. The name WhiteSource didn't have any negative connotations when the company was founded, but some people today find it offensive.

Security Affairs
MAY 25, 2022
The Nigeria Police Force has arrested the suspected leader of the SilverTerrier cybercrime group as a result of an international operation. The Nigeria Police Force has arrested the suspected leader of the SilverTerrier cybercrime gang (aka TMT ) after a year-long investigation codenamed “Operation Delilah.” SilverTerrier has been active since at least 2014 and focuses on BEC attacks, it is a collective of over hundreds of individual threat actors.

Data Breach Today
MAY 25, 2022
Indian Airline Says Attack on IT Infrastructure 'Contained'; Threat Actor Unknown Indian passenger airline SpiceJet says an attempt at a ransomware attack was made against its IT infrastructure on Tuesday night. The airline says the attack was "contained," and it has resumed regular operations. Passengers continued to complain about takeoff delays until noon local time.

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.

Dark Reading
MAY 25, 2022
With manufacturing ranking as the fourth most targeted sector, manufacturers that understand their exposure will be able to build the necessary security maturity.

KnowBe4
MAY 25, 2022
Scammers are using deepfake videos of Elon Musk in an attempt to trick people into handing over cryptocurrency, BleepingComputer reports. The scammers set up a phony cryptocurrency platform called “BitVex” that purports to be owned by Musk. The crooks then used hacked YouTube accounts to spread deepfaked videos of Musk and other people associated with cryptocurrency to promote the platform.

Dark Reading
MAY 25, 2022
Google has disclosed a nasty set of six bugs affecting Zoom chat that can be chained together for MitM and RCE attacks, no user interaction required.

Hanzo Learning Center
MAY 25, 2022
Organizations create and share enormous volumes of sensitive information, and with the rise of SaaS applications and collaboration tools, this information can exist in many places: emails, Slack messages, Jira tickets, Salesforce records, internal HR databases, Asana projects, and anywhere else work is getting done.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

Dark Reading
MAY 25, 2022
This year's finalists tackle such vital security concerns as permissions management, software supply chain vulnerability, and data governance. Winners will be announced June 6.

Jamf
MAY 25, 2022
Marking its fifteenth year, Verizon’s Data Breach Investigations Report analyzes data breach demographics spread across multiple industry verticals, providing results based on breach cases and incidents reviewed. The data gleaned from its analysis provides organizations insight into what threat types are driving attacks and how trends play a significant role over time in security.

Outpost24
MAY 25, 2022
Penetration Testing To Prevent API Attack. 27.May.2022. Florian Barre. Wed, 05/25/2022 - 07:12. Anthony Ippolito, Security Consultant, Outpost24. Ghost Labs. Teaser. This blog describes the attack path we have uncovered during a recent penetration test of a web application, coupled with a back-end infrastructure assessment. Throughout we introduce different attack techniques and tools that can be used to attack the underlying infrastructure and APIs of a web application.
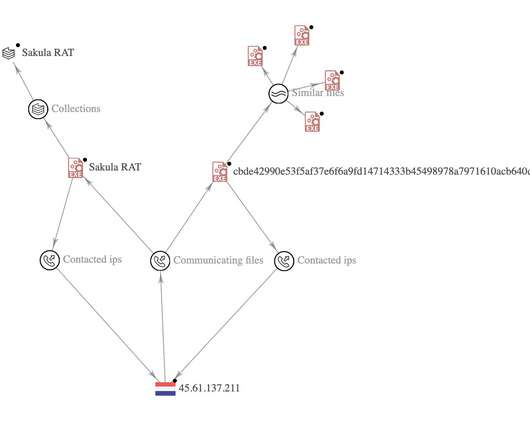
Security Affairs
MAY 25, 2022
An unknown APT group is targeting Russian government entities since the beginning of the Russian invasion of Ukraine. Researchers from Malwarebytes observed an unknown Advanced Persistent Threat (APT) group targeting Russian government entities with at least four separate spear-phishing campaigns since the beginning of the Russian invasion of Ukraine.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.
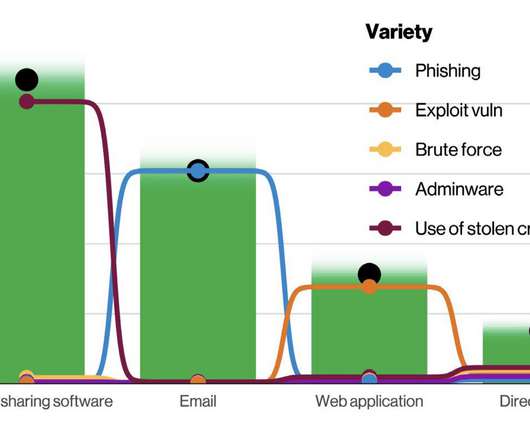
KnowBe4
MAY 25, 2022
With the much-anticipated annual Verizon Data Breach Investigations Report finally released, we get a view of ransomware from the data breach perspective that points to a common weakness in your security strategy.

eSecurity Planet
MAY 25, 2022
Intrusion detection system (IDS) and intrusion prevention system (IPS) technologies – often combined as intrusion detection and prevention (IDPS) – have been in use for decades, yet they remain important cybersecurity tools even in the face of today’s rapidly changing cyber threats and complex IT environments. An ideal security stack provides continuous protection without gaps.

Threatpost
MAY 25, 2022
2022’s DBIR also highlighted the far-reaching impact of supply-chain breaches and how organizations and their employees are the reasons why incidents occur.

Dark Reading
MAY 25, 2022
A sprawling, multiyear operation nabs a suspected SilverTerrier BEC group ringleader, exposing a massive attack infrastructure and sapping the group of a bit of its strength.

Advertisement
If you’re considering migrating from DataStax Enterprise (DSE) to open source Apache Cassandra®, our comprehensive guide is tailored for architects, engineers, and IT directors. Whether you’re motivated by cost savings, avoiding vendor lock-in, or embracing the vibrant open-source community, Apache Cassandra offers robust value. Transition seamlessly to Instaclustr Managed Cassandra with our expert insights, ensuring zero downtime during migration.

Data Protection Report
MAY 25, 2022
In this article we distil critical lessons from the Federal Court’s recent decision in Australian Securities and Investments Commission v RI Advice Group Pty Ltd [1] and practical actions to be taken by Boards and executive management. Boards and organisations should assess their cybersecurity risk management activities in light of the decision and ask whether current approaches are adequately resourced and operating effectively?

Dark Reading
MAY 25, 2022
Supply chain and ransomware attacks increased dramatically in 2021, which explains why so many data breaches in Verizon's "2022 Data Breach Investigations Report" were grouped as system intrusion.

OpenText Information Management
MAY 25, 2022
Don’t miss this year’s keynote presentation with OpenText CEO and CTO, Mark Barrenechea, and SAP CEO and member of the SAP Executive board, Christian Klein, at OpenText World EMEA. Mark and Christian will discuss some of the challenges we are all facing and how the partnership between SAP and OpenText can help solve these issues, … The post Why SAP customers should attend OpenText World EMEA appeared first on OpenText Blogs.

Dark Reading
MAY 25, 2022
Purporting to publish leaked emails of pro-Brexit leadership in the UK, a new site's operations have been traced to Russian cyber-threat actors, Google says.

Advertisement
Are you trying to decide which entity resolution capabilities you need? It can be confusing to determine which features are most important for your project. And sometimes key features are overlooked. Get the Entity Resolution Evaluation Checklist to make sure you’ve thought of everything to make your project a success! The list was created by Senzing’s team of leading entity resolution experts, based on their real-world experience.

The Security Ledger
MAY 25, 2022
In this episode of the podcast (#238) we speak with Daniel Brodie, the CTO at the firm Cynerio. about his firm’s discovery of a string of critical security flaws in an autonomous medical robot, TUG, that is already deployed in hundreds of clinical settings and the growing issue of medical device insecurity and cyber risks to healthcare. Read the whole entry. » Click the icon below to listen.

Dark Reading
MAY 25, 2022
Implement zero-trust policies for greater control, use BYOD management tools, and take proactive steps such as keeping apps current and training staff to keep sensitive company data safe and employees' devices secure.

IG Guru
MAY 25, 2022
Check out the post here. The post U.S. DOJ will no longer prosecute ethical hackers under CFAA via Bleeping Computer appeared first on IG GURU.
Let's personalize your content