Ransomware Payments: Just 46% of Victims Now Pay a Ransom
Data Breach Today
MAY 5, 2022
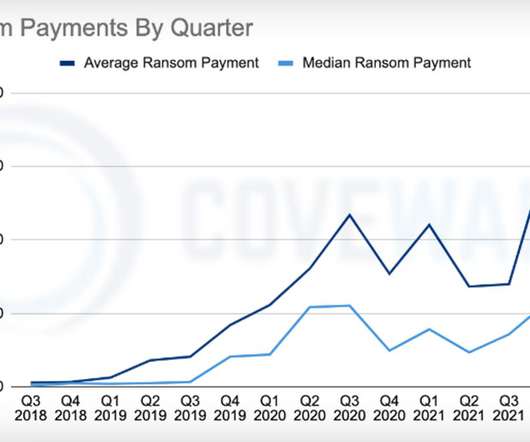
Average Ransom Payment, When a Victim Pays, Drops to $211,529, Coveware Reports Two signs that the tide may finally, if slowly, be turning on ransomware: The number of victims who choose to pay continues to decline, while the amount they pay - when they choose to do so - recently dropped by one-third, reports ransomware incident response firm Coveware.





































Let's personalize your content