 The number one way that hackers and malware compromise people, devices, and networks is social engineering. No one argues that anymore, but it was not always known or discussed that way. Even though social engineering has been the number one way hackers and malware exploit people and devices since the beginning of network computers, it was not generally known or discussed as such until just five or 10 years ago. Yes, everyone knew it was a big cybersecurity problem, but most people did not know it was the number one problem…by far.
The number one way that hackers and malware compromise people, devices, and networks is social engineering. No one argues that anymore, but it was not always known or discussed that way. Even though social engineering has been the number one way hackers and malware exploit people and devices since the beginning of network computers, it was not generally known or discussed as such until just five or 10 years ago. Yes, everyone knew it was a big cybersecurity problem, but most people did not know it was the number one problem…by far.
Depending on the source you read, social engineering is responsible for 40% to over 90% of all cyberattacks. There is strong evidence that social engineering is involved in the upper range of estimates. This article is about that fact.
I first stated that social engineering was involved in 70% to 90% of all successful breaches back in 2020. Back then, I was told I was insane by many readers. Although they believed social engineering was the top threat (or at least a top threat), they did not believe it could be so high. But I had not made the claim lightly.
My data was based upon years of research, where I tracked thousands of breaches listed in the Privacy Rights Clearinghouse Database and tied them to their initial root causes. It was not always easy to determine an initial root cause for a variety of reasons. First, not all breaches included a root cause in the database or related public reports. In those cases, I tried to email or call people involved in the case to get root causes. Other times, the root causes were incorrectly described. For example, many breaches were incorrectly tied to “email attacks” or “ransomware”. Those are outcomes of initial root causes, not root causes themselves. I would have to ask people, “How did the ransomware get into your company?” Sometimes they knew, sometimes they did not. But in the cases where I could determine an initial root cause exploit, social engineering was involved in at least 70% of the cases.
Note: Unpatched software and firmware was involved in 20% to 40% of the cases. Recently, Mandiant said unpatched software and firmware were involved in 33% of successful breaches, so the percentages seem to be holding.
Also, in my career, I was given access to huge proprietary databases of multiple companies who were involved in investigating thousands or more data breaches. Those databases also backed the high prevalence of social engineering in most attacks. My claim was not made lightly. It was not just a gut feeling.
Since then, the status of social engineering being the number one root exploit cause by far has only been backed up. My KnowBe4 colleague, Javvad Malik, did a meta-analysis study of one hundred vendor reports (from 43 different vendors) he retrieved from AlienVault’s Open Threat Exchange. The percentage of attacks attributed to social engineering varied by report and vendor, but in a vast majority of cases, social engineering was the top threat.
Example Reports
This is still the case in nearly every vendor report I read which discusses hacking root causes. Most do not agree on the percentage, but they all agree that social engineering/phishing is the number one root hacking method. Here are some examples:
A 2022 SecureWorks report found that the number of incident response cases they were involved in doubled between 2021 and 2022, mostly because of business email compromise (BEC) scams, and 85% of those BEC scams were due to social engineering.
This August, Comcast reported that 89.46% of attacks on their customers started with phishing.
IBM’s 2023 X-Force Threat Intelligence Index report had phishing at a much lower percentage stating, “Phishing remains the leading infection vector, identified in 41% of incidents, followed by exploitation of public-facing applications in 26%.” Their 2022 report had stated much of the same, “Phishing continued to be the most prevalent initial access vector identified…” and “…phishing served as the initial infection vector in 78% of incidents X-Force responded to across these industries so far in 2022.”
The UK’s Official Government Statistics Cyber Security Breaches Survey 2022 stated the following, “…the most common threat vector was phishing attempts (83%).
In 2022, Kroll’s Cyber Intelligence Report stated that phishing was involved in 60% of all attacks.
InfoBlox’s 2022 Global State of Security Report states, “The most successful mode of attack was phishing (58%).”
In May 2023, Barracuda Networks reported that although spear phishing only accounted for 0.1% of all email-based attacks, it accounted for 66% of successful compromises. That is huge for a single root cause!
So, much like Javvad Malik’s meta-study revealed, vendors may not agree on the exact percentages, but they agree phishing is the number cyber threat, and it is a big one.
Why Do Social Engineering Statistics Vary So Much?
The primary reason different vendors report different social engineering statistics is the customers involved and the scope of the survey. Some vendors only include customers that they did business with. Some, like the UK report, are only surveying their country’s organizations. Others simply focus on a particular industry or customer size.
Another big reason is because, sadly, there is no agreed upon set of initial root cause access categories. Many times, the vendors categorize a particular type of attack as a root access method when really it is the outcome of a root access method. For example, many vendors would have a category called ransomware, remote access, or credential theft. All of those are outcomes of other root access methods. For example, if credential theft was involved, how did the credentials get stolen? I can tell you. Probably social engineering. There is a good chance that if all vendors agreed to use the same category descriptions that their social engineering categories would be larger than they report.
It Is Likely Larger, Much Larger!
It is likely that the social engineering stats that are reported, large as they already are, are drastically undercounting the true breadth of social engineering. This is for a bunch of reasons. For one, most vendor reports only report on corporate or industry customers. Most reports do not survey people at home using their personal computers and phones. If they did, they would likely find that most have been attempted victims of social engineering, often through email, but also through SMS texting. Who among us has not been phished at home through our email, SMS messages, and even voice calls? Some days most of my text messages are scams. Most calls I get to my phone are scams. Anyone been asked to extend their auto warranty lately? How many of us have had our parents and grandparents successfully scammed?
If nearly everyone you know has been approached to be scammed via email and phone, how much larger should the social engineering stat be? Most people on social media (e.g., Facebook, Instagram, etc.) are routinely approached with scams on those services. I get an attempted scam on LinkedIn nearly every day. Have you ever tried to sell or buy something on Craigslist? The first contact you are likely to get is from a scammer. I have had a ton of friends who were either successfully scammed or almost scammed when trying to rent an apartment or vacation stay.
How about romance scams? The FTC reported that over 70,000 people lost over $1.3B to romance scams in 2022. And these are just the people who reported it to the FTC, which has to be a tiny percentage of the total number of victims.
I think if any single source aggregated all types of initial root hacking methods across both personal and industry interests, the total amount of social engineering would be up in the high 90s. When nearly 100% of us have experienced an attempted scam each year, how could there have been any other result?
The Solution
Teach yourself, your coworkers, your friends, your family, how to recognize social engineering scams and how to treat them (e.g, ignore, delete, report, etc.). Because social engineering can happen from almost any angle, you must teach everyone to have a healthy level of skepticism, especially with new messages. Here is a good, simple flowchart to share:
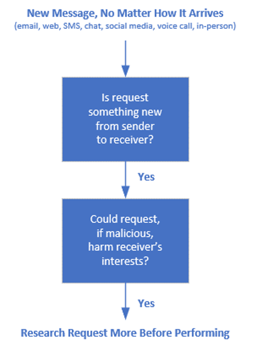
We strongly recommend training everyone with lots of examples of different types of social engineering. The more examples and types of social engineering they are exposed to, the less likely they are to be scammed by a malicious actor. The key is education, education, education.
Do not let the scammer be the only one introducing scams to your coworkers and friends.
 The 2024 Phishing By Industry Benchmarking Report compiles results from the seventh annual study by KnowBe4 and reveals at-risk users across 19 industries that are susceptible to phishing or social engineering attacks. Taking it a step further, the research reveals radical drops in careless clicking after 90 days and 12 months of simulated phishing testing and security awareness training using the KnowBe4 platform.
The 2024 Phishing By Industry Benchmarking Report compiles results from the seventh annual study by KnowBe4 and reveals at-risk users across 19 industries that are susceptible to phishing or social engineering attacks. Taking it a step further, the research reveals radical drops in careless clicking after 90 days and 12 months of simulated phishing testing and security awareness training using the KnowBe4 platform.




