Data Breach Roundup: Attempted Extortion Attack on Dragos
Data Breach Today
MAY 11, 2023
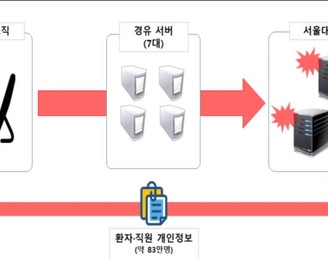
Also: Twitter Hacker Pleads Guilty, Seoul National University Hospital and Sysco In this week's data breach, the spotlight was on Dragos, a guilty plea from a Twitter hacker and cryptocurrency thief and North Korean hackers. Also, Sysco, a Ukrainian border truck queuing system and an update on Western Digital. Plus, a new tool for decrypting partially encrypted files.








































Let's personalize your content