Frebniis malware abuses Microsoft IIS feature to create a backdoor
Security Affairs
FEBRUARY 19, 2023
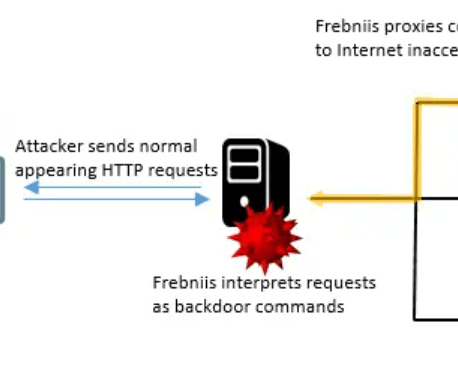
Experts spotted a malware dubbed Frebniis that abuses a Microsoft IIS feature to deploy a backdoor and monitor all HTTP traffic to the system. Broadcom Symantec researchers have spotted a new malware, tracked as Frebniis, that abuses Microsoft Internet Information Services (IIS) to deploy a backdoor and monitor all HTTP traffic to the infected system, Symantec reports.














Let's personalize your content