Will Third-Party App Stores Play With Apple's Walled Garden?
Data Breach Today
DECEMBER 15, 2022
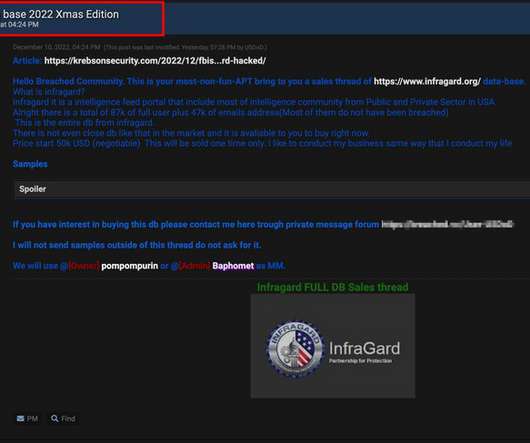
EU Legislation Says Mobile Platforms Must Grant Access to Third-Party Apps, Stores Apple is advancing plans to allow Europeans to access third-party app stores via their iPhone and iPad, as will soon be required under European law. What this means in practice for its vaunted walled garden security model, and whether most users will bother, remains unclear.








































Let's personalize your content