Cyber Threats Are Evolving
Data Breach Today
OCTOBER 13, 2022
By working together, we can contribute to a safer world. Cyber threats are evolving. By working together, we can contribute to a safer world.

Data Breach Today
OCTOBER 13, 2022
By working together, we can contribute to a safer world. Cyber threats are evolving. By working together, we can contribute to a safer world.

Data Matters
OCTOBER 13, 2022
On October 5, 2022, a federal jury in the Northern District of California convicted former Uber Chief Security Officer Joseph Sullivan of obstructing a federal proceeding and misprision of a felony for his role in deceiving management and the federal government to cover up a 2016 data breach that exposed personally identifiable information (“PII”) of approximately 57 million users, including approximately 600,000 drivers’ license numbers, of the ride-hailing service.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Data Breach Today
OCTOBER 13, 2022
Hardenize to Help Red Sift Customers Assess Security of Domains and Certificates A phishing and fraud prevention vendor has bought a startup founded by Qualys' longtime engineering leader to help organizations more effectively discover and monitor assets. Red Sift says its purchase of Hardenize will help customers assess the security of their digital asset inventory.

Dark Reading
OCTOBER 13, 2022
The comprehensive, multiplatform framework comes loaded with weapons, and it is likely another effort by a China-based threat group to develop an alternative to Cobalt Strike and Sliver.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.

Data Breach Today
OCTOBER 13, 2022
The latest ISMG Security Report examines whether banks should be held liable for the rapidly increasing Zelle fraud problem, explores the latest M&A activity among IAM vendors, and discusses the implications of the new legal framework for personal data transfers between the U.S. and Europe.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

Data Breach Today
OCTOBER 13, 2022
CEO Yotam Segev says Cyera eschews the focus of data loss prevention tools on blocking users from pulling down data and instead embraces an approach that reduces friction. Cyera has sought to safeguard data by making preventative changes in areas like configuration, permissions and security posture.
Security Affairs
OCTOBER 13, 2022
Cloudflare mitigated a record distributed denial-of-service (DDoS) attack against Wynncraft, one of the largest Minecraft servers. Cloudflare announced it has mitigated a record distributed denial-of-service (DDoS) attack against Wynncraft, one of the largest Minecraft servers. The Cloudflare DDoS threat report 2022 Q3 states that multi-terabit massive DDoS attacks have become increasingly frequent.

Data Breach Today
OCTOBER 13, 2022
White House Shows Increased Interest in Standards for Critical Infrastructure, IoT The Biden administration will put more critical infrastructure sectors, such as water, under mandates to ensure minimal cybersecurity standards. The White House is also ramping up interest in consumer cybersecurity by initiating a labeling program for the internet of things.
Security Affairs
OCTOBER 13, 2022
Kaspersky researchers warn of a recently discovered malicious version of a popular WhatsApp messenger mod dubbed YoWhatsApp. Kaspersky researchers discovered an unofficial WhatsApp Android application named ‘YoWhatsApp’ that steals access keys for users’ accounts. Mod apps are advertised as unofficial versions of legitimate apps that have features that the official one does not supports.

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.

Data Breach Today
OCTOBER 13, 2022
Also: Why Some Facilities Are Affected While Others Are Not The toll that cyber incidents can have on healthcare entities and their patients was especially felt this week by the parents of a 3-year-old child who received an accidental megadose of medicine - a mistake attributed to IT systems being offline at an Iowa medical center.

IT Governance
OCTOBER 13, 2022
This week, we discuss yet more planned changes to UK data protection law, a £1.35 million GDPR fine for “predatory marketing”, the conviction of Uber’s former chief security officer, and a new book about how to establish an enjoyable career. Now available on Spotify , Amazon Music , Apple Podcasts and SoundCloud. The post IT Governance Podcast Episode 10: Data protection reform, Easylife fine, Uber conviction and work appeared first on IT Governance UK Blog.

Data Breach Today
OCTOBER 13, 2022
Consorci Sanitari Integral Says It Is Fully Recovered From Ransomware Attack A ransomware gang published 22 gigabytes of data it says it stole from Consorci Sanitari Integral, a Barcelona health organization of 3,000 physicians and staff. CSI acknowledge a "compromise in data confidentiality" but says its systems are fully recovered thanks to cloud backups.

Dark Reading
OCTOBER 13, 2022
The campaign uses a combination of tactics and a common JavaScript obfuscation technique to fool both end users and email security scanners to steal credentials.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

KnowBe4
OCTOBER 13, 2022
INKY has published a report on the use of small business grants as phishing lures. Scammers are impersonating the US Small Business Administration (SBA) to distribute phony grant applications hosted on Google Forms.

Dark Reading
OCTOBER 13, 2022
Can already beleaguered CISOs now add possible legal charges to their smorgasbord of job considerations? Disclose a breach to comply and face dismissal, or cover it up and face personal punishment.

KnowBe4
OCTOBER 13, 2022
Scammers have been around as long as history has been recorded. Think about the famous ‘Trojan Horse’ for example. A perfect scam that allowed attackers to get behind the city walls. The same is still happening, although the technology has evolved from wooden horses to digital ones. Even with the change in technology, deception, especially that which uses emotions to deceive, has not.

WIRED Threat Level
OCTOBER 13, 2022
The Infowars host now knows the cost of “free speech”—but does the landmark judgment signal a crackdown on disinformation?

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.
Security Affairs
OCTOBER 13, 2022
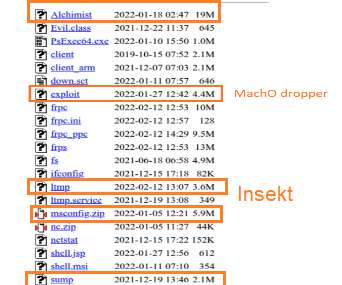
Experts discovered a new attack framework, including a C2 tool dubbed Alchimist, used in attacks against Windows, macOS, and Linux systems. Researchers from Cisco Talos discovered a new, previously undocumented attack framework that included a C2 dubbed Alchimist. The framework is likely being used in attacks aimed at Windows, macOS, and Linux systems.

Dark Reading
OCTOBER 13, 2022
Ransomware attacks are on the rise, but organizations also have access to advanced tools and technologies they can use to fight back.

Data Matters
OCTOBER 13, 2022
On October 5, 2022, a federal jury in the Northern District of California convicted former Uber Chief Security Officer Joseph Sullivan of obstructing a federal proceeding and misprision of a felony for his role in deceiving management and the federal government to cover up a 2016 data breach that exposed personally identifiable information (“PII”) of approximately 57 million users, including approximately 600,000 drivers’ license numbers, of the ride-hailing service.

Dark Reading
OCTOBER 13, 2022
From the basics to advanced techniques, here's what you should know.

Advertisement
If you’re considering migrating from DataStax Enterprise (DSE) to open source Apache Cassandra®, our comprehensive guide is tailored for architects, engineers, and IT directors. Whether you’re motivated by cost savings, avoiding vendor lock-in, or embracing the vibrant open-source community, Apache Cassandra offers robust value. Transition seamlessly to Instaclustr Managed Cassandra with our expert insights, ensuring zero downtime during migration.

WIRED Threat Level
OCTOBER 13, 2022
By releasing half a million users’ transactions in a bankruptcy court filing, the company has opened a vast breach in its users’ financial privacy.

Dark Reading
OCTOBER 13, 2022
Electric Vehicle Charging Station Leader Certified in Accordance with ISO/SAE 21434 "Road Vehicles – Cybersecurity Engineering".

OpenText Information Management
OCTOBER 13, 2022
Both technology providers and customers increasingly recognize the importance of onboarding to start the journey of adopting new technology on the right foot. But what makes for a successful onboarding experience? Donna Weber, The Customer Onboarding Expert, has written extensively on this topic. She stresses that onboarding is “much more than deploying your product”.

Dark Reading
OCTOBER 13, 2022
SaaS security platform promises to track down shadow IT, map supply chain risk, and "nudge" employees to work securely.

Advertisement
Are you trying to decide which entity resolution capabilities you need? It can be confusing to determine which features are most important for your project. And sometimes key features are overlooked. Get the Entity Resolution Evaluation Checklist to make sure you’ve thought of everything to make your project a success! The list was created by Senzing’s team of leading entity resolution experts, based on their real-world experience.

Zapproved
OCTOBER 13, 2022
Corporate legal teams take on many responsibilities, but risk mitigation is among the most critical. One of the most important blips on the risk radar is the spoliation of evidence. Whenever your company faces the possibility of civil litigation, any company data that may potentially serve as evidence must be preserved. In the context of […].

Dark Reading
OCTOBER 13, 2022
A timing attack helps cyberattackers lob malicious code-bombs at corporate targets by cloning private package names.

Unwritten Record
OCTOBER 13, 2022
On October 14, 1947, USAF Captain Charles E. “Chuck” Yeager became the first person to fly faster than the speed of sound. Yeager flew a Bell X-1, nicknamed “Glamorous Glennis” (a tribute to his wife), over Rogers Dry Lake located at Edward’s Air Force Base (formerly named Muroc Air Force Base). The X-1 reached a speed of 700 miles per hour and an altitude of 43,000 feet.
Let's personalize your content