How to Use Signal Encrypted Messaging
WIRED Threat Level
AUGUST 18, 2022
The best end-to-end encrypted messaging app has a host of security features. Here are the ones you should care about.

WIRED Threat Level
AUGUST 18, 2022
The best end-to-end encrypted messaging app has a host of security features. Here are the ones you should care about.
Krebs on Security
AUGUST 18, 2022
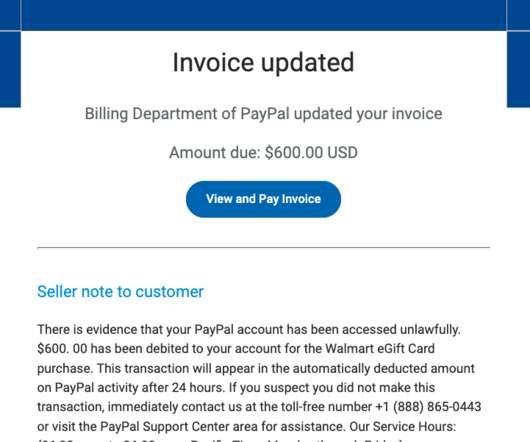
Scammers are using invoices sent through PayPal.com to trick recipients into calling a number to dispute a pending charge. The missives — which come from Paypal.com and include a link at Paypal.com that displays an invoice for the supposed transaction — state that the user’s account is about to be charged hundreds of dollars. Recipients who call the supplied toll-free number to contest the transaction are soon asked to download software that lets the scammers assume remote cont
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Data Breach Today
AUGUST 18, 2022
Advisory Comes in Midst of Recent Cyber Incidents Involving Cloud Providers With healthcare sector entities increasingly transitioning to cloud-based applications, storage and various other third-party hosted services, they must be proactive in addressing a list of associated security risks, U.S. federal authorities urge. What are the top recommendations?
Security Affairs
AUGUST 18, 2022
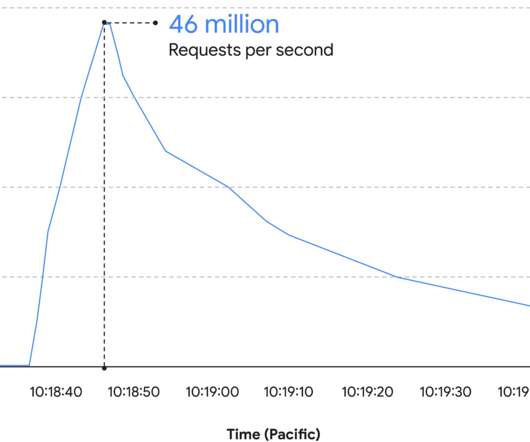
Google announced to have blocked the largest ever HTTPs DDoS attack, which reached 46 million requests per second (RPS). Google announced to have blocked the largest ever HTTPs DDoS attack that hit one of its Cloud Armor customers. The IT giant revealed that the attack reached 46 million requests per second (RPS). The attack took place on June 1st, at 09:45, it started with more than 10,000 requests per second (rps) and targeted a customer’s HTTP/S Load Balancer.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.

Data Breach Today
AUGUST 18, 2022
Ukrainian Official: Country Hit By Over 1,600 'Major Cyber Incidents' This Year A crowded field of 51 threat groups in the Russia-Ukraine cyberwar has attacked 29 nations - with attacks in Ukraine aimed at "sowing chaos and confusion" on and off the battlefield. This special report covers the tactics, techniques and motivations of threat actors and fallout for other nations.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

Data Breach Today
AUGUST 18, 2022
Denis Dubnikov Allegedly Laundered $400,000 in Ransom Proceeds Denis Mihaqlovic Dubnikov, 29, allegedly participated in a conspiracy to launder money obtained through Ryuk ransomware. Operators behind the malware mounted one of the largest cyberattacks against the healthcare sector in a fall 2021 ransomware spree.

Security Affairs
AUGUST 18, 2022
Apple released Safari 15.6.1 for macOS Big Sur and Catalina to address a zero-day vulnerability actively exploited in the wild. Safari 15.6.1 for macOS Big Sur and Catalina addressed an actively exploited zero-day vulnerability tracked as CVE-2022-32893. The flaw is an out-of-bounds write issue in WebKit and the IT giant fixed it with improved bounds checking.

Data Breach Today
AUGUST 18, 2022
Victor Zhora, Deputy Head of Ukraine's Cyber Agency, Shares Lessons Learned As the Russia-Ukraine war continues, Ukrainian government cybersecurity official Victor Zhora says that the country's computer emergency response team has tracked more than 1,600 online attacks and that defensively, "wipers continue to be the biggest challenge.

Security Affairs
AUGUST 18, 2022
Apple addressed two zero-day vulnerabilities, exploited by threat actors, affecting iOS, iPadOS , and macOS devices. Apple this week released security updates for iOS, iPadOS , and macOS platforms to address two zero-day vulnerabilities exploited by threat actors. Apple did not share details about these attacks. The two flaws are: CVE-2022-32893 – An out-of-bounds issue in WebKit which.

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.

Data Breach Today
AUGUST 18, 2022
Fortinet's Douglas Santos on Latest Trends From Global Threat Landscape Report Fortinet’s FortiGuard Labs released the latest Global Threat Landscape Report - a view of events observed during the first half of 2022. Learn how actors target vulnerabilities, build malicious infrastructure and exploit their targets. The report also covers threat trends affecting IT and OT.

KnowBe4
AUGUST 18, 2022
Tailgating or piggybacking is an old but effective social engineering technique to gain physical access to restricted areas, according to Rahul Awati at TechTarget. Tailgating is when a bad actor simply follows an employee through a door that requires authentication.

Data Breach Today
AUGUST 18, 2022
Company Has Laid Off 125 Employees to Refocus on Small and Midsized Customers Malwarebytes laid off 125 employees to refocus its business on small and midsized customers. The company has been unable to grow its meager market share in the corporate endpoint security market and didn't make Gartner's or Forrester's latest endpoint security vendor roundups.

Security Affairs
AUGUST 18, 2022
A new version of the BlackByte ransomware appeared in the threat landscape, version 2.0 uses extortion techniques similar to LockBit ones. BlackByte ransomware Version 2.0 appeared in the threat landscape after a short break, the latest version has a new data leak site. It is interesting to note that the group introduced some novelties in the extortion strategy.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

IT Governance
AUGUST 18, 2022
Internal audits are essential for maintaining ISO 27001 compliance. The requirements for writing an internal audit report are outlined in Clause 9.2 of the Standard. But how do ISO 27001 audits work, and why do you need to document the results? We explain everything you need to know in this blog, including our top tips for writing an ISO 27001 internal audit report.

Security Affairs
AUGUST 18, 2022
Exploit code for a critical vulnerability affecting networking devices using Realtek RTL819x system on a chip released online. The PoC exploit code for a critical stack-based buffer overflow issue, tracked as CVE-2022-27255 (CVSS 9.8), affecting networking devices using Realtek’s RTL819x system on a chip was released online. The issue resides in the Realtek’s SDK for the open-source eCos operating system, it was discovered by researchers from cybersecurity firm Faraday Security. “On Realte

DLA Piper Privacy Matters
AUGUST 18, 2022
Google LLC has agreed to pay AUD 60 million to Australia’s competition regulator, the Australian Competition and Consumer Commission ( ACCC ), after it was held that Google breached the Australian Consumer Law ( ACL ) regarding its collection of location data. In October 2019, the ACCC commenced proceedings alleging that Google had engaged in misleading and deceptive conduct and made false or misleading representations to consumers between January 2017 and December 2018 in respect of the way loc

IT Governance
AUGUST 18, 2022
This week, we discuss a ransomware attack on an NHS digital services provider and a huge increase in cyber attacks as a result of the war in Ukraine, and provide an overview of the main reforms to UK data protection law proposed by the Digital Protection and Information Bill. Now available on Spotify , Amazon Music , Apple Podcasts and SoundCloud.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.

Dark Reading
AUGUST 18, 2022
The state-sponsored threat actor has switched up its tactics, also adding an automated SQL-injection tool to its bag of tricks for initial access.

Adapture
AUGUST 18, 2022
The CRN 2022 Fast Growth 150 List Recognizes Atlanta-Based IT Solutions Provider ADAPTURE for Exceptional Growth and Performance ATLANTA, Aug. 18, 2022 – CRN, a brand of The Channel Company, has recognized ADAPTURE on its 2022 Fast Growth 150 list. The Fast Growth 150 list acknowledges the fastest-growing and highest-performing channel solution providers, technology integrators, IT consultants, and service providers in North America.

Dark Reading
AUGUST 18, 2022
The cybercriminal crew has used 15 malware families to target travel and hospitality companies globally, constantly changing tactics over the course of its four-year history.

KnowBe4
AUGUST 18, 2022
New data shows attempted ransomware attacks are occurring far more frequently while a lack of confidence is found in security measures and solutions to stop ransomware attacks.

Advertisement
If you’re considering migrating from DataStax Enterprise (DSE) to open source Apache Cassandra®, our comprehensive guide is tailored for architects, engineers, and IT directors. Whether you’re motivated by cost savings, avoiding vendor lock-in, or embracing the vibrant open-source community, Apache Cassandra offers robust value. Transition seamlessly to Instaclustr Managed Cassandra with our expert insights, ensuring zero downtime during migration.

The Security Ledger
AUGUST 18, 2022
We speak with Mikko Hyppönen on the sidelines of the DEF CON Conference in Las Vegas to talk about his new book, “If its Smart it Vulnerable.". The post Episode 241: If Its Smart, Its Vulnerable a Conversation with Mikko Hyppönen appeared first on The Security Ledger with Paul F. Roberts. Click the icon below to listen. Related Stories Episode 241: If Its Smart, Its Vulnerable a Conversation wit Mikko Hyppönen Feel Good Ukraine Tractor Story Highlights Ag Cyber Risk DEF CON DOOM Patrol: Dee

KnowBe4
AUGUST 18, 2022
Plenty of new anecdotal and legal case-based stories are demonstrating that just because your organization has a policy doesn’t mean it’s actually going to pay out after an attack.

WIRED Threat Level
AUGUST 18, 2022
The Freedom of Information Act helps Americans learn what the government is up to. The Poseys exploited it—and became unlikely defenders of transparency.

KnowBe4
AUGUST 18, 2022
New data shows an upswell of email-based cyberattacks, with over 256 brands being impersonated, as social media, Microsoft, shipping, and ecommerce brands top the list.

Advertisement
Are you trying to decide which entity resolution capabilities you need? It can be confusing to determine which features are most important for your project. And sometimes key features are overlooked. Get the Entity Resolution Evaluation Checklist to make sure you’ve thought of everything to make your project a success! The list was created by Senzing’s team of leading entity resolution experts, based on their real-world experience.

Threatpost
AUGUST 18, 2022
An insufficient validation input flaw, one of 11 patched in an update this week, could allow for arbitrary code execution and is under active attack.

Troy Hunt
AUGUST 18, 2022
Right off the back of a visit to our wedding venue (4 weeks and counting!) and a few hours before heading to the snow (yes, Australia has snow), I managed to slip in a weekly update earlier today. I've gotta say, the section on Shitexpress is my favourite because there's just so much to give with this one; a service that literally ships s**t with a public promise of multiple kinds of animal s**t whilst data that proves only horse s**t was ever shipped, a promise of 100% anonymity whils

Jamf
AUGUST 18, 2022
Jamf was on-hand at Black Hat 2022 to meet with customers and discuss the modern security landscape directly with the Security and IT professionals themselves. See what they had to say about the current state of security at their organizations when asked about it in Jamf’s anonymous survey conducted right from the showroom floor.
Let's personalize your content