When Efforts to Contain a Data Breach Backfire
Krebs on Security
AUGUST 16, 2022
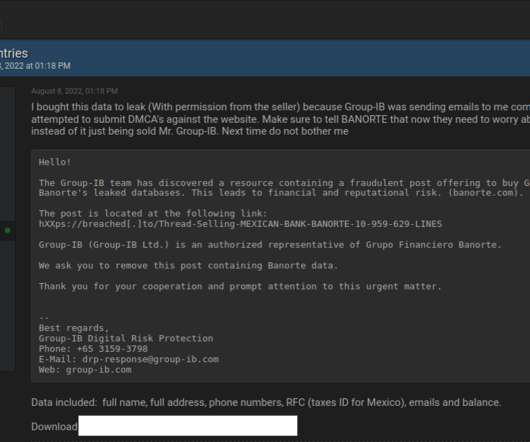
Earlier this month, the administrator of the cybercrime forum Breached received a cease-and-desist letter from a cybersecurity firm. The missive alleged that an auction on the site for data stolen from 10 million customers of Mexico’s second-largest bank was fake news and harming the bank’s reputation. The administrator responded to this empty threat by purchasing the stolen banking data and leaking it on the forum for everyone to download.








































Let's personalize your content