New WhatsApp Scam Uses Call Forwarding Social Engineering to Hijack Accounts
KnowBe4
JULY 7, 2022
This is a great example of how even the simplest of social engineering tactics can be used as the first step in a likely-larger scam.

KnowBe4
JULY 7, 2022
This is a great example of how even the simplest of social engineering tactics can be used as the first step in a likely-larger scam.
Data Breach Today
JULY 7, 2022
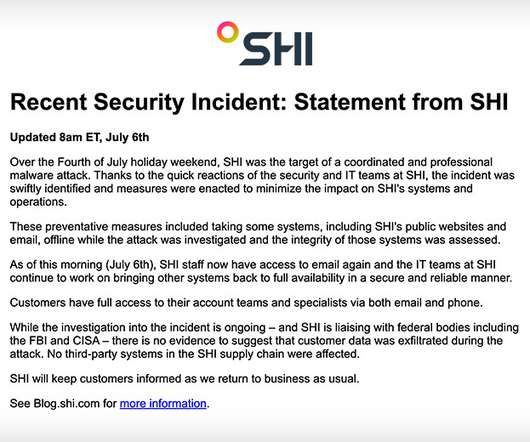
SHI Took Its Public Websites and Email Offline to Assess the System Integrity A "coordinated and professional malware attack" against SHI left the company without email or public websites for days while the hack was investigated. SHI took its public websites and email offline after being hit during the July Fourth holiday weekend to assess the integrity of those systems.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Dark Reading
JULY 7, 2022
It's time to tap the large reservoir of talent with analytical skills to help tackle cybersecurity problems. Train workers in cybersecurity details while using their ability to solve problems.
Data Breach Today
JULY 7, 2022
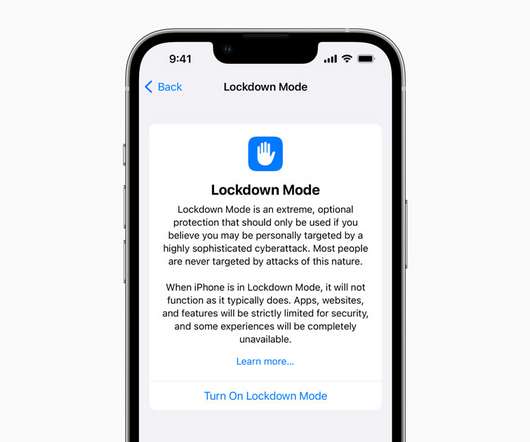
'Extreme' Digital Security Coming for Activists and Journalists Lockdown Mode will be available to all users who update to the latest versions of Apple operating systems this fall. This "extreme" protection will stop spyware infections through restrictions that render message attachments inaccessible, webpages slower to load and FaceTime calls harder to make.

Advertisement
Many organizations today are unlocking the power of their data by using graph databases to feed downstream analytics, enahance visualizations, and more. Yet, when different graph nodes represent the same entity, graphs get messy. Watch this essential video with Senzing CEO Jeff Jonas on how adding entity resolution to a graph database condenses network graphs to improve analytics and save your analysts time.
Security Affairs
JULY 7, 2022
Cybersecurity researchers warn of new malware, tracked as OrBit, which is a fully undetected Linux threat. Cybersecurity researchers at Intezer have uncovered a new Linux malware, tracked as OrBit, that is still undetected. The malware can be installed as a volatile implant either by achieving persistence on the compromised systems. The malware implements advanced evasion techniques and hooks key functions to maintain persistence on the infected systems.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

Security Affairs
JULY 7, 2022
US authorities have issued a joint advisory warning of North Korea-linked APTs using Maui ransomware in attacks against the Healthcare sector. The FBI, CISA, and the U.S. Treasury Department issued a joint advisory that warn of North-Korea-linked threat actors using Maui ransomware in attacks aimed at organizations in the Healthcare sector. “The Federal Bureau of Investigation (FBI), Cybersecurity and Infrastructure Security Agency (CISA), and the Department of the Treasury (Treasury) are

Data Breach Today
JULY 7, 2022
Google Plans to Delete Certain Location Data; What Can Other Entities Do? Google's move to soon begin deleting location history pertaining to individuals' visits to facilities offering sensitive healthcare services is a step in the right direction, but experts say technology firms and others could do more to better protect the privacy of health data.

Dark Reading
JULY 7, 2022
Improper implementations of authentication APIs at a global crypto wallet service provider could have resulted in the loss of account control — and millions of dollars — from personal and business accounts.

Data Breach Today
JULY 7, 2022
'The Chinese Government Is Set on Stealing Your Technology,' Says FBI Director Wray FBI Director Christopher Wray and MI5 Director General Ken McCallum put business and academic leaders on alert over Chinese government-led intellectual property theft, telling an audience in London to think twice about doing business with Beijing.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.

OpenText Information Management
JULY 7, 2022
Welcome to OpenText. We are the information company. We power and protect information to elevate every person and every organization to gain the information advantage. In this day and time, information is ubiquitous and everywhere. It is scattered throughout organizations. Structured and unstructured. Tracked and untracked. Internal and external. In fact, there is so much … The post Discover your Information Advantage appeared first on OpenText Blogs.

Data Breach Today
JULY 7, 2022
Adam Wedgbury of Airbus on Effective Ways Humans Can Boost Cybersecurity Posture Raising user awareness is too often incorrectly considered to be a panacea for faulty information security programs. "It can drive risk reduction, but it is not the primary driver of risk reduction," says Adam Wedgbury, head of enterprise security architecture at Airbus.

Security Affairs
JULY 7, 2022
The development team behind the OpenSSL project fixed a high-severity bug in the library that could potentially lead to remote code execution. The maintainers of the OpenSSL project fixed a high-severity heap memory corruption issue , tracked as CVE-2022-2274 , affecting the popular library. This bug makes the RSA implementation with 2048 bit private keys incorrect on such machines and triggers a memory corruption during the computation.

Threatpost
JULY 7, 2022
A radio control system for drones is vulnerable to remote takeover, thanks to a weakness in the mechanism that binds transmitter and receiver.

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.
Security Affairs
JULY 7, 2022
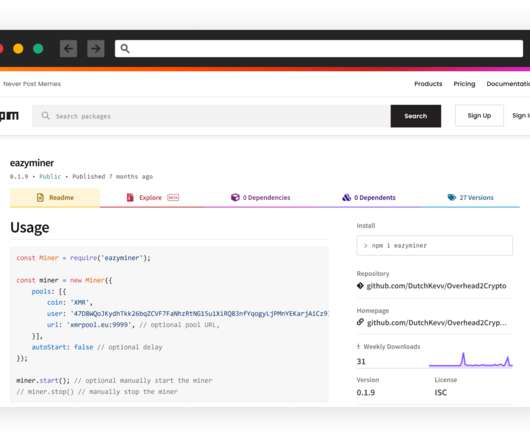
Researchers uncovered a large-scale cryptocurrency mining campaign targeting the NPM JavaScript package repository. Checkmarx researchers spotted a new large-scale cryptocurrency mining campaign, tracked as CuteBoi , that is targeting the NPM JavaScript package repository. Threat actors behind the campaign published 1,283 malicious modules in the repository and used over 1,000 different user accounts.

IT Governance
JULY 7, 2022
This week, we discuss new NCSC guidance on avoiding cyber security “staff burnout”, a data breach affecting a Japanese city’s entire population, good news for the ransomware-hit Maastricht University, and the privacy implications of the metaverse. The post IT Governance Podcast Episode 3: NCSC guidance, Amagasaki data breach, Maastricht University and the metaverse appeared first on IT Governance UK Blog.

Schneier on Security
JULY 7, 2022
Report by Georgetown’s Center on Privacy and Technology published a comprehensive report on the surprising amount of mass surveillance conducted by Immigration and Customs Enforcement (ICE). Our two-year investigation, including hundreds of Freedom of Information Act requests and a comprehensive review of ICE’s contracting and procurement records, reveals that ICE now operates as a domestic surveillance agency.
Dark Reading
JULY 7, 2022
The latest criminal use of a legitimate red-teaming tool helps attackers stay under the radar and better access living-off-the-land binaries.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

KnowBe4
JULY 7, 2022
The lure of last-minute deals to get away after staying home for the last 2 years is so strong, scammers are using it to their advantage with scams intent on stealing online credentials.

WIRED Threat Level
JULY 7, 2022
Known as ALPRs, this surveillance tech is pervasive across the US—and could soon be used by police and anti-abortion groups alike.

Dark Reading
JULY 7, 2022
With the world potentially less than a decade away from breaking current encryption around critical data, researchers weigh in on planning for the post-quantum world.

KnowBe4
JULY 7, 2022
Researchers at CloudSEK have observed a financially motivated phishing campaign that’s impersonating the United Arab Emirates (UAE) Ministry of Human Resources. The large-scale campaign is targeting organizations in the “Finance, Travel, Hospital, Legal, Oil and Gas, and Consultation industries.”.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.

Dark Reading
JULY 7, 2022
In a significant spike of activity, the state-sponsored group is going after intelligence on Russian government agencies.

KnowBe4
JULY 7, 2022
Cybersecurity Culture is a hot topic amongst many organisations and security professionals. But what are organisations doing to build a strong security culture ?

Security Affairs
JULY 7, 2022
I’m proud to announce that the European Union Agency for Cybersecurity, ENISA, has released the Threat Landscape Methodology. Policy makers, risk managers and information security practitioners need up-to-date and accurate information on the current threat landscape, supported by threat intelligence. The EU Agency for Cybersecurity (ENISA) Threat Landscape report has been published on an annual basis since 2013.

Dark Reading
JULY 7, 2022
New program offers free tech skills training and paid apprenticeships to make education and career pathways more accessible.

Advertisement
If you’re considering migrating from DataStax Enterprise (DSE) to open source Apache Cassandra®, our comprehensive guide is tailored for architects, engineers, and IT directors. Whether you’re motivated by cost savings, avoiding vendor lock-in, or embracing the vibrant open-source community, Apache Cassandra offers robust value. Transition seamlessly to Instaclustr Managed Cassandra with our expert insights, ensuring zero downtime during migration.

KnowBe4
JULY 7, 2022
Bloomberg recently reported that FBI Director Christopher Wray issued a warning to Western companies that China wants to 'ransack' their IP. The goal of this attack would be to dominate key industries.

IG Guru
JULY 7, 2022
Check out the article here. The post Modernizing Mahoning: Thousands of paper land records to be digitized via Vindy.com appeared first on IG GURU.

Dark Reading
JULY 7, 2022
When examining the modern threat landscape, empowering your security operations and overcoming the limitations inherent with other malware prevention solutions is imperative.
Let's personalize your content