Design Weakness Discovered in Apple M1 Kernel Protections
Dark Reading
JUNE 10, 2022
The proof-of-concept attack from MIT CSAIL researchers undermines the pointer authentication feature used to defend the Apple chip's OS kernel.

Dark Reading
JUNE 10, 2022
The proof-of-concept attack from MIT CSAIL researchers undermines the pointer authentication feature used to defend the Apple chip's OS kernel.

Data Breach Today
JUNE 10, 2022
Company Becomes the 3rd Late-Stage Startup to Cut Headcount in the Past 3 Weeks OneTrust has laid off 25% of its staff - or 950 workers - making it the third late-stage startup to significantly cut headcount in recent weeks. The Atlanta-based privacy and data governance vendor says the capital markets want to see a more balanced approach between growth and profitability.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Krebs on Security
JUNE 10, 2022
At the outset of their federal criminal trial for hijacking vast swaths of Internet addresses for use in large-scale email spam campaigns, three current or former executives at online advertising firm Adconion Direct (now Amobee ) have pleaded guilty to lesser misdemeanor charges of fraud and misrepresentation via email. In October 2018, prosecutors in the Southern District of California named four Adconion employees — Jacob Bychak , Mark Manoogian , Petr Pacas , and Mohammed Abdul Qayyum
Data Breach Today
JUNE 10, 2022
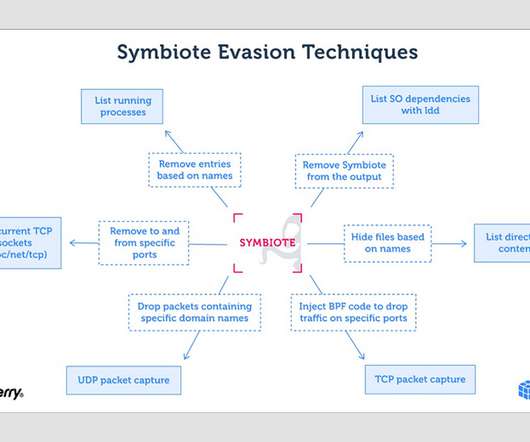
Highly Evasive Symbiote Can Hide Itself and Other Malware Post-Infection New malware called Symbiote is affecting Linux operating systems by infecting other running processes to inflict damage on machines, say Intezer security researcher Joakim Kennedy and the BlackBerry Threat Research and Intelligence Team, who jointly conducted the research.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.
Dark Reading
JUNE 10, 2022
Next-generation AI products learn proactively and identify changes in the networks, users, and databases using "data drift" to adapt to specific threats as they evolve.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.
Security Affairs
JUNE 10, 2022
The Cuba ransomware operators are back and employed a new version of its malware in recent attacks. Cuba ransomware has been active since at least January 2020. Its operators have a data leak site, where they post exfiltrated data from their victims who refused to pay the ransom. The ransomware encrypts files on the targeted systems using the “.cuba” extension.

Data Breach Today
JUNE 10, 2022
Denise Anderson, President and CEO of H-ISAC, on Industry Progress, New Risks While ransomware, third-party risk, phishing scams and insiders continue as the top threats facing healthcare and public health entities, the sector overall is becoming better prepared to deal with these issues than it was just a few years ago, says Denise Anderson, president and CEO of H-ISAC.
Security Affairs
JUNE 10, 2022
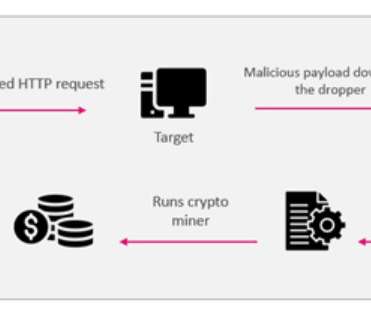
Threat actors are exploiting the recently disclosed CVE-2022-26134 RCE in Atlassian Confluence servers to deploy cryptocurrency miners. CheckPoint researchers have observed threat actors exploiting the recently disclosed CVE-2022-26134 remote code execution vulnerability in Atlassian Confluence servers to deploy cryptocurrency miners. Last week, Atlassian warned of a critical unpatched remote code execution vulnerability affecting all Confluence Server and Data Center supported versions, tracked

Data Breach Today
JUNE 10, 2022
Workaround Guidance, Temporary Fix Now Available for the Vulnerabilities Microsoft has not yet released patches for two zero-days, Follina and DogWalk, that both exploit vulnerabilities in the Microsoft Windows Support Diagnostic Tool. But the company has released a workaround for Follina, and micropatching service 0Patch has offered a temporary fix for DogWalk.

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.
Security Affairs
JUNE 10, 2022
The Vice Society group has claimed responsibility for the ransomware attack that hit the Italian city of Palermo forcing the IT admins to shut down its infrastructure. The Vice Society ransomware group has claimed responsibility for the recent cyber attack that hit the city of Palermo in the South of Italy. In response to the security breach, the IT infrastructure of the city was shut down.
Dark Reading
JUNE 10, 2022
So-called Symbiote malware, first found targeting financial institutions, contains stealthy rootkit capabilities.

Record Nations
JUNE 10, 2022
Nearly every industry has strict protocols when it comes to record keeping. There are a number of industries that have strict government oversight when it comes to record management, while other industries take a state by state approach. This is the case when it comes to landlords and rental agencies. Even though the rules tend […]. The post Record Keeping: A Guide for Landlords appeared first on Record Nations.

Dark Reading
JUNE 10, 2022
In 1985, a group of klezmer musicians from the US rendezvoused with underground dissidents in Tbilisi, Georgia. This is the story of how they pulled it off with homebrew cryptography.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

Outpost24
JUNE 10, 2022
A History of Ransomware. 13.Jun.2022. Florian Barre. Fri, 06/10/2022 - 06:20. Jose Miguel Esparza, Head of Threat Intelligence at Blueliv, an Outpost company. Threat Intelligence. Teaser. Ransomware is the biggest cyber threat to businesses. First burst onto the scene in 1989, it has evolved significantly over the past few years from widespread attacks to highly targeted ransomware-as-a-service (RaaS) operations affecting organizations of all sizes and sectors.

Dark Reading
JUNE 10, 2022
The commission argues that legislative action is needed to ensure a well-functioning market for AI systems that balances benefits and risks.

WIRED Threat Level
JUNE 10, 2022
The House committee's televised hearings interrogate the Capitol attack with damning new evidence. Whether it's enough to prevent another one is uncertain.

Dark Reading
JUNE 10, 2022
Cisco's TK Keanini and the NFL's Tomás Maldonado join Dark Reading's Terry Sweeney at Dark Reading News Desk during RSA Conference to talk about end-to-end security.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.

WIRED Threat Level
JUNE 10, 2022
Twitter has reportedly given the billionaire access to its full stream of tweets and related user data. Is your privacy in jeopardy?

Threatpost
JUNE 10, 2022
The dangerous malware appears to be well and truly back in action, sporting new variants and security-dodging behaviors in a wave of recent phishing campaigns.

Dark Reading
JUNE 10, 2022
Raytheon Intelligence & Space's Jon Check joins Dark Reading's Terry Sweeney at Dark Reading News Desk at RSA Conference to talk about how hiring must change.

IG Guru
JUNE 10, 2022
Check out the link here. The post Microsoft Trying to Kill HDD Boot Drives By 2023: Report via Tom’s Hardware appeared first on IG GURU.

Advertisement
If you’re considering migrating from DataStax Enterprise (DSE) to open source Apache Cassandra®, our comprehensive guide is tailored for architects, engineers, and IT directors. Whether you’re motivated by cost savings, avoiding vendor lock-in, or embracing the vibrant open-source community, Apache Cassandra offers robust value. Transition seamlessly to Instaclustr Managed Cassandra with our expert insights, ensuring zero downtime during migration.

Dark Reading
JUNE 10, 2022
Cloud migration, DevSecOps, cyber insurance, and more have emerged as important motivators for cybersecurity investment and focus.

Threatpost
JUNE 10, 2022
Environmentalists and policymakers warn water treatment plants are ripe for attack.

Dark Reading
JUNE 10, 2022
Humio for Falcon provides long-term, cost-effective data retention with powerful index-free search and analysis of enriched security telemetry across enterprise environments

Gimmal
JUNE 10, 2022
Reinventing Professionals , a podcast hosted by industry analyst, Ari Kaplan , shares ideas, guidance, and perspectives from market leaders shaping the next generation of legal and professional services. Craig Carpenter and Dean Gonsowski , Gimmal’s CEO and CRO respectively, spoke with Ari about information discovery, migration, governance, and compliance, and how Gimmal helps organization address their biggest information governance challenges.

Advertisement
Are you trying to decide which entity resolution capabilities you need? It can be confusing to determine which features are most important for your project. And sometimes key features are overlooked. Get the Entity Resolution Evaluation Checklist to make sure you’ve thought of everything to make your project a success! The list was created by Senzing’s team of leading entity resolution experts, based on their real-world experience.

Dark Reading
JUNE 10, 2022
Mend's Arabella Hallawell joins Dark Reading's Terry Sweeney at Dark Reading News Desk at RSA Conference to talk about the benefits of automated remediation.

Data Protection Report
JUNE 10, 2022
On May 25 th 2022, the European Commission published a series of questions and answers on the SCCs to be used between controllers and processors within the European Economic Area ( EEA ), and the SCCs to be used for transfers to countries not considered adequate by the European Commission ( Third Countries ) (the Q&As ). The text of the Q&As is available here.

Dark Reading
JUNE 10, 2022
Halcyon's Jon Miller joins Dark Reading's Terry Sweeney at Dark Reading News Desk during RSA Conference to discuss how to mitigate ransomware.
Let's personalize your content