First US Sanction of a Virtual Currency Mixer: Blender.io
Data Breach Today
MAY 9, 2022
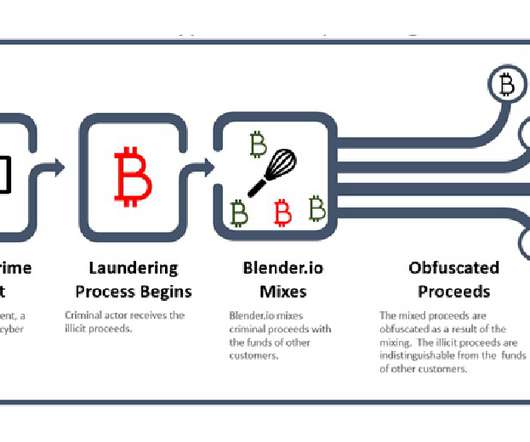
Treasury Says North Korea's Lazarus Group Used Mixer to Launder Stolen Crypto Virtual currency mixer Blender.io has been sanctioned by the U.S. for enabling North Korea to conduct "malicious cyber activities and money laundering of stolen virtual currency," the U.S. Treasury Department’s Office of Foreign Assets Control says in its first sanctioning of a currency mixer.


































Let's personalize your content