 A new phishing campaign impersonates MetaMask, informs victims their cryptocurrency wallets aren’t “verified” and threatens suspension.
A new phishing campaign impersonates MetaMask, informs victims their cryptocurrency wallets aren’t “verified” and threatens suspension.
Cybercriminals will go wherever they a) perceive the money is and b) wherever they have expertise in the scam. In the case of the latest attack on MetaMask users identified by security researchers at Bitdefender Labs, the mastermind behind this attack certainly understands how MetaMask works.
In the scam, the potential victim user is sent an email impersonating MetaMask, asking for their wallet to be verified:
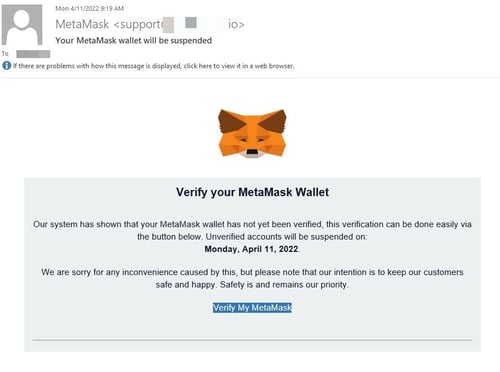
Those that click the “Verify My MetaMask” are taken to a phishing site made to look like MetaMask’s website. On the site, the victim is asked to provide their recovery phrase (a sequence of ten random words established when the wallet is setup that can be used to recover access to the wallet should the credentials be lost).
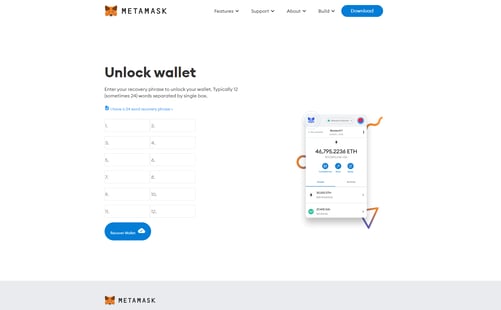
Once the recovery phrase is provided, it’s game over for the wallet owner, and funds are difficult to recover.
The key to the success of this campaign is found in the urgency it creates; the threat of suspending the wallet if it is not verified is enough to make unsuspecting recipients of this phishing email act accordingly and give up their most secret details about their MetaMask wallet.
This use of urgency is found in nearly every phishing scam – whether targeting individuals or users within an organization. And it’s only through having a vigilant mindset when receiving an email like the one above that will cause the recipient to pause and scrutinize the email to determine whether it’s legitimate or not before following the instructions found within. This vigilance is established in organizations through continual Security Awareness Training designed to not just teach users that scams are everywhere, but how they work, what role the user themselves plays in a phishing attack, and how they can stop the attack by simply paying attention.
 Here's how it works:
Here's how it works:




