What the Conti Ransomware Group Data Leak Tells Us
Dark Reading
MARCH 24, 2022
Knowing the inner workings of Conti will not only help ransomware negotiators but also help organizations to better handle a ransomware attack when it happens.

Dark Reading
MARCH 24, 2022
Knowing the inner workings of Conti will not only help ransomware negotiators but also help organizations to better handle a ransomware attack when it happens.

Data Breach Today
MARCH 24, 2022
Lapsus$ Gained Access to a Sitel Support Engineer's Computer Via Remote Hosting Okta says it should have notified customers of a breach earlier and that Lapsus$ compromised a laptop belonging to Sitel, a third-party customer support firm, via remote desktop protocol, enabling it to infiltrate Okta's network. Cybersecurity experts discuss the impact of the breach and offer mitigation advice.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

The Last Watchdog
MARCH 24, 2022
It can be a real hassle to keep track of the passwords you use. So many people use the same combination of username and password for every account. However, this isn’t a good idea. In fact, it’s terrible. Related: Kaseya hack exacerbates supply chain exposures. You see, these days, many data breaches could be traced back to people using the same password across multiple accounts.
Data Breach Today
MARCH 24, 2022
The latest edition of the ISMG Security Report reviews the latest cyber resilience "call to action" from the White House and also explores authentication provider Okta's failure to inform hundreds of customers in a timely manner that their data could have been stolen by the Lapsus$ group.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.

Jamf
MARCH 24, 2022
With 2021 in the rearview, we revisit the biggest threats businesses faced during the year. In looking back, we summarize both macOS and mobile endpoint security threats along with their impact. We also turn an eye toward the future by focusing on the upcoming threats the enterprise will be facing, such as ransomware as a service, and on how Jamf can help you prevent security threats.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

KnowBe4
MARCH 24, 2022
When it's time to complete a compliance audit, are you thinking, "Ugh, is it that time again?". And, as more organizations demand proof that their data is protected in the cloud, keeping up with risk assessments and audits to prove compliance is a continuous problem.

Hunton Privacy
MARCH 24, 2022
On March 24, 2022, Utah became the fourth state in the U.S., following California, Virginia and Colorado, to enact a consumer data privacy law, the Utah Consumer Privacy Act (the “UCPA”). The UCPA resembles Virginia’s Consumer Data Protection Act (“VCDPA”) and Colorado’s Consumer Privacy Act (“CPA”), and, to a lesser extent, the California Consumer Privacy Act (as amended by the California Privacy Rights Act) (“CCPA/CPRA”).

Security Affairs
MARCH 24, 2022
The Anonymous hacker collective claims to have hacked the Central Bank of Russia and stole accessed 35,000 documents. Anonymous continues to target Russian government organizations and private businesses, now it is claiming to have hacked the Central Bank of Russia. The popular hacker collective claims to have compromised the systems of the Central Bank of Russia and stole 35,000 files, it announced that will leak it it in 48 hours.

Data Matters
MARCH 24, 2022
* This article first appeared in Legaltech News on March 22, 2024, available here. With federal consumer privacy bills gaining little traction, the Uniform Law Commission proposes the Uniform Personal Data Protection Act (UPDPA) as an alternative to the existing quilt of state consumer privacy laws. In a panel hosted by Sidley Austin partner Alan Raul, the drafters discussed the major features of the law and how they balance consumer concerns about data privacy while reducing commercial disrupti

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.

KnowBe4
MARCH 24, 2022
Scammers continue to exploit the crisis in Ukraine, according to researchers at Bitdefender. Over the past week, the researchers believe the fraudsters have adjusted their tactics in response to increased media coverage of these scams.

Record Nations
MARCH 24, 2022
Do you know Record Nations? Whether we’ve worked with you for years, or you’re new to the business, we thought it was high time we introduced you to some of the people behind the brand. While we may have been in business for roughly two decades, a lot has changed over the years. We’ve incorporated […]. The post Who We Are – Scott Reis: VP of Partner Development and Advocacy appeared first on Record Nations.

Data Protection Report
MARCH 24, 2022
The UK Government has added two new duties to the proposed Online Safety Bill (the Bill ) that are aimed at protecting people against anonymous online abuse. These measures would give users of “main social media firms” more control over who can interact with them and the type of content users see (see the Government’s press release of 25 February 2022 ).

IT Governance
MARCH 24, 2022
Three quarters of UK residents are concerned about their online safety, according to a study by the cyber security firm Surfshark. That figure might not come as a surprise, given the growing awareness of data privacy. There are regular news stories of data breaches, while the GDPR (General Data Protection Regulation) has changed the way organisations handle personal data.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

KnowBe4
MARCH 24, 2022
WIRED wrote: " More than 22,000 miles above Earth, the KA-SAT is locked in orbit. Traveling at 7,000 miles per hour, in sync with the planet’s rotation, the satellite beams high-speed internet down to people across Europe.
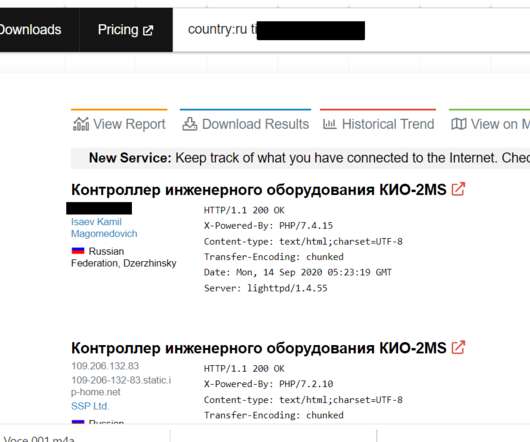
Security Affairs
MARCH 24, 2022
A researcher discovered critical flaws that can be exploited by remote attackers to hack a building controller popular in Russia. A researcher has identified critical vulnerabilities that can allegedly be exploited to remotely hack a building controller predominantly used by organizations in Russia. Researcher Jose Bertin discovered critical flaws affecting a controller made by Russian company Tekon Avtomatika which is widely used by organizations in Russia.

KnowBe4
MARCH 24, 2022
Fidelity just published an article titled " Cybersecurity: A growing risk ". They note that the threat of Russian cyberattacks highlights vulnerabilities across industries. I'm quoting a small section and I suggest you read the rest of the article here.

Threatpost
MARCH 24, 2022
~30 crypto companies were affected, including BlockFi, Swan Bitcoin and NYDIG, providing an uncomfortable reminder about how much data CRM systems snarf up.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.

Dark Reading
MARCH 24, 2022
Four Russian government employees were charged by the DoJ for attack campaigns targeting hundreds of energy sector companies and organizations in 135 countries, including the US.

Security Affairs
MARCH 24, 2022
Anonymous launches its offensive against Wester companies still operating in Russia, it ‘DDoSed’ Auchan, Leroy Merlin e Decathlon websites. Since the start of the Russian invasion of Ukraine on February 24, Anonymous has declared war on Russia and launched multiple cyber-attacks against Russian entities, including Russian government sites , state-run media websites , and energy firms.

Dark Reading
MARCH 24, 2022
Stay one step ahead of the constantly evolving cyber threats with the right MSP email security solution. Discover how to evaluate and select the best service and solutions for your clients.

KnowBe4
MARCH 24, 2022
Google’s Threat Analysis Group (TAG) describes a cybercriminal group it calls “EXOTIC LILY” that acts as an initial access broker for numerous financially motivated threat actors, including FIN12 and the Conti ransomware gang. EXOTIC LILY uses phishing attacks to gain access to organizations’ networks, then sells this access to other gangs for further exploitation.

Advertisement
If you’re considering migrating from DataStax Enterprise (DSE) to open source Apache Cassandra®, our comprehensive guide is tailored for architects, engineers, and IT directors. Whether you’re motivated by cost savings, avoiding vendor lock-in, or embracing the vibrant open-source community, Apache Cassandra offers robust value. Transition seamlessly to Instaclustr Managed Cassandra with our expert insights, ensuring zero downtime during migration.

WIRED Threat Level
MARCH 24, 2022
The Justice Department unsealed indictments against four alleged Russian hackers said to have targeted US energy infrastructure for nearly a decade.

Security Affairs
MARCH 24, 2022
VMware addressed two critical arbitrary code execution vulnerabilities affecting its Carbon Black App Control platform. VMware released this week, software updates to address two critical security vulnerabilities, CVE-2022-22951 and CVE-2022-22952 (both received a CVSS score of 10), affecting its Carbon Black App Control platform that could be exploited by a threat actor to execute arbitrary code on affected installations on Windows systems.

Threatpost
MARCH 24, 2022
Mustang Panda's already sophisticated cyberespionage campaign has matured even further with the introduction of a brand-new PlugX RAT variant.

OpenText Information Management
MARCH 24, 2022
In software implementation projects, the focus is increasingly shifting towards user adoption, applying ‘people change management’ best practices to reach this goal. There is a lot to say about people change management principles and best practices that we have previously discussed (How change management, adapting and adoption became a daily task & 7 ways to … The post Identify your biggest contributor to successful user adoption appeared first on OpenText Blogs.

Advertisement
Are you trying to decide which entity resolution capabilities you need? It can be confusing to determine which features are most important for your project. And sometimes key features are overlooked. Get the Entity Resolution Evaluation Checklist to make sure you’ve thought of everything to make your project a success! The list was created by Senzing’s team of leading entity resolution experts, based on their real-world experience.

Hunton Privacy
MARCH 24, 2022
On March 15, 2022, the Federal Trade Commission (FTC) announced a proposed settlement with custom merchandise platform CafePress in connection with the company’s alleged failure to implement reasonable security measures, and its alleged attempt to cover up a 2019 data breach. The proposed settlement would require CafePress to implement a comprehensive data security program and pay $500,000 in redress to affected individuals.

IG Guru
MARCH 24, 2022
Check out the article here. The post CISA adds 15 vulnerabilities to list of flaws exploited in attacks via Bleeping Computer appeared first on IG GURU.

CGI
MARCH 24, 2022
This CGI blog post shares three recommendations for moving toward next-generation credit management.
Let's personalize your content