Who Wrote the ALPHV/BlackCat Ransomware Strain?
Krebs on Security
JANUARY 28, 2022
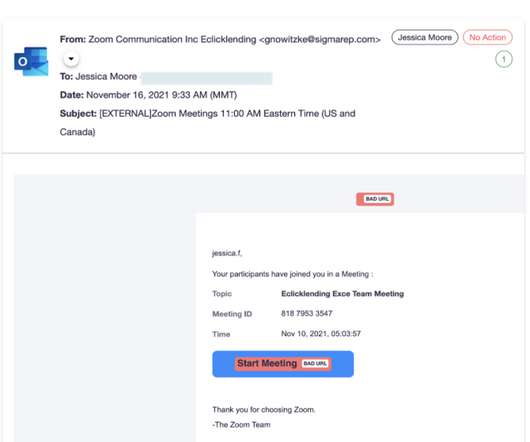
In December 2021, researchers discovered a new ransomware-as-a-service named ALPHV (a.k.a. “ BlackCat “), considered to be the first professional cybercrime group to create and use a ransomware strain written in the Rust programming language. In this post, we’ll explore some of the clues left behind by a developer who was reputedly hired to code the ransomware variant.

































Let's personalize your content