HackDHS bug bounty program accepts reports of Log4j-related flaws in DHS systems
Security Affairs
DECEMBER 23, 2021
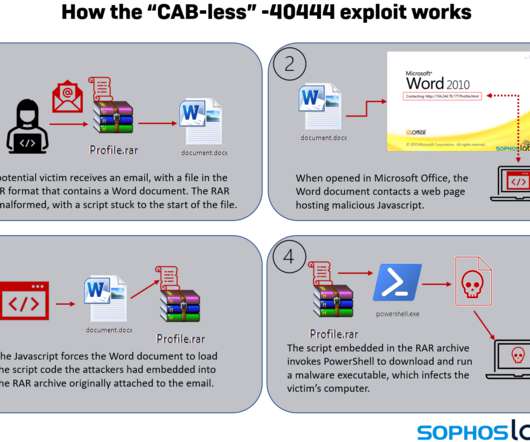
The DHS has announced that it is expanding the ‘Hack DHS’ bug bounty program to report for Log4J impacting its systems. The Department of Homeland Security (DHS) announced that white hat hackers can now report the impact of the Log4J on its systems as part of the ‘ Hack DHS ‘ bug bounty program. Below is the announcement of DHS Secretary Alejandro N.
























Let's personalize your content