3 Ways to Deal With the Trojan Source Attack
Dark Reading
NOVEMBER 8, 2021
These scripts and commands provide short-term fixes for blocking the Trojan Source attack that abuses Unicode to inject malicious backdoors in source code.
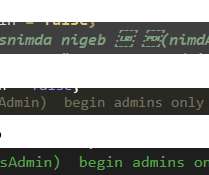
Dark Reading
NOVEMBER 8, 2021
These scripts and commands provide short-term fixes for blocking the Trojan Source attack that abuses Unicode to inject malicious backdoors in source code.

Krebs on Security
NOVEMBER 8, 2021
The U.S. Department of Justice today announced the arrest of Ukrainian man accused of deploying ransomware on behalf of the REvil ransomware gang, a Russian-speaking cybercriminal collective that has extorted hundreds of millions from victim organizations. The DOJ also said it had seized $6.1 million in cryptocurrency sent to another REvil affiliate, and that the U.S.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

The Last Watchdog
NOVEMBER 8, 2021
There’s no doubt, the increasing use of telemedicine, the explosion of health-based cloud apps, and innovative medical IoT devices are improving the patient care experience. Related: Hackers relentlessly target healthcare providers. However, healthcare data ranks at the top of the list for needing improvements in security and privacy protections. This data is managed by different entities, such as primary care facilities, acute care facilities and within associated applications that collect, sto

Security Affairs
NOVEMBER 8, 2021
The US DoJ has charged a REvil ransomware affiliate that is suspected to have orchestrated the attack on Kaseya MSP platform in July. The US Department of Justice has charged a REvil ransomware affiliate for orchestrating the ransomware attacks on Kaseya MSP platform that took place in July 4. The suspect is 22-year old Ukrainian national Yaroslav Vasinskyi (aka Profcomserv, Rabotnik, Rabotnik_New, Yarik45, Yaraslav2468, and Affiliate 22), who was arrested for cybercriminal activity on October 8

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.

OpenText Information Management
NOVEMBER 8, 2021
While public clouds offer a breadth of benefits such as cost savings, scalability, and flexibility, many government entities are hesitant to make the leap. As of 2019, only 11% of federal IT systems are running in the cloud, and less than 5% of private government clouds are experiencing the full breadth of benefits available from cloud adoption. This is largely due to security, privacy, … The post The big challenges in wide-scale government cloud adoption appeared first on OpenText Blogs.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

Threatpost
NOVEMBER 8, 2021
The U.S. is seeking the extradition of a Ukrainian man, Yaroslav Vasinskyi, whom they suspect is behind the Kaseya supply-chain attacks and other REvil attacks.

Security Affairs
NOVEMBER 8, 2021
Electronics retail giant MediaMarkt was hit by a ransomware attack that disrupted store operations in the Netherlands and Germany. Electronics retail giant MediaMarkt was a victim of a ransomware attack that forced the company to shut down its IT infrastructure to contain the threat and disrupted store operations in the Netherlands and Germany. Media Markt is a German multinational chain of stores selling consumer electronics with over 1000 stores in Europe.

Dark Reading
NOVEMBER 8, 2021
Incentives for good conduct and deterrents for bad behavior in cyberspace are impossible to effectively establish and enforce without international collaboration and commitment.

Hunton Privacy
NOVEMBER 8, 2021
On November 2, 2021, Facebook parent Meta Platforms Inc. announced in a blog post that it will shut down its “ Face Recognition” system in coming weeks as part of a company-wide move to limit the use of facial recognition in its products. The company cited the need to “weigh the positive use cases for facial recognition against growing societal concerns, especially as regulators have yet to provide clear rules.”.

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.

eSecurity Planet
NOVEMBER 8, 2021
The McAfee consumer security business, which trades on the NASDAQ under the symbol MCFE, will be going private in a deal valued at more than $14 billion. McAfee had sold its Enterprise business just a few months ago, to a private consortium led by Symphony Technology Group (STG) – and McAfee Enterprise was subsequently merged with the FireEye security products business that STG acquired from Mandiant (MNDT).

Security Affairs
NOVEMBER 8, 2021
The healthcare industry might be known for the work it does to treat patients. But it is also a prime target for malicious cyber actors. With copious amounts of data collected by healthcare facilities, cybercriminals often target such entities. Moreover, the healthcare industry collects unique data, known as Protected Health Information (PHI), which is extremely valuable.

Dark Reading
NOVEMBER 8, 2021
Now is the time for organizations to rethink their security strategies with a platform- and architecture-based approach in mind. Keanini explains.

WIRED Threat Level
NOVEMBER 8, 2021
By arresting one alleged hacker associated with REVil and seizing millions from another, the US has made it clear that ransomware comes with a cost.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

Dark Reading
NOVEMBER 8, 2021
The data shows security leaders are focusing on multilayered defenses, including multifactor authentication, threat intelligence, and incident response.

Security Affairs
NOVEMBER 8, 2021
Operation Cyclone – Six alleged affiliates with the Clop ransomware operation were arrested in an international joint law enforcement operation led by Interpol. Interpol announced the arrest of six alleged affiliates with the Clop ransomware operation as part of an international joint law enforcement operation codenamed Operation Cyclone. Law enforcement authorities from South Korea, Ukraine, and the United States, joint their efforts in a 30-month investigation that was coordinated by Int

Threatpost
NOVEMBER 8, 2021
Researchers have uncovered a large, tangled web of infrastructure being used to enable a wide variety of cyberattacks.

Security Affairs
NOVEMBER 8, 2021
The FBI warns of an increase of fraudulent schemes leveraging cryptocurrency ATMs and QR Codes to facilitate payment. The FBI Internet Crime Complaint Center (IC3) published an alert to warn the public of fraudulent schemes leveraging cryptocurrency ATMs and Quick Response (QR) codes to complete payment transactions. This payment option makes it quite impossible to recover the money stolen with fraudulent schemes. “The FBI warns the public of fraudulent schemes leveraging cryptocurrency AT

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.

IG Guru
NOVEMBER 8, 2021
Check out the article here. The post GUEST ESSAY: Tapping Bitcoin’s security — to put a stop to ‘51% attacks’ of cryptocurrency exchanges via Information Management Today appeared first on IG GURU.

Threatpost
NOVEMBER 8, 2021
A new campaign is prying apart a known security vulnerability in the Zoho ManageEngine ADSelfService Plus password manager, researchers warned over the weekend. The threat actors have managed to exploit the Zoho weakness in at least nine global entities across critical sectors so far (technology, defense, healthcare, energy and education), deploying the Godzilla webshell and […].

Dark Reading
NOVEMBER 8, 2021
The group, made up of Advent, Permira, Crosspoint Capital, CPP Investments, GIC, and ADIA, will take ownership of McAfee.

Hunton Privacy
NOVEMBER 8, 2021
Beginning in 2022, Apple and Google will impose new privacy requirements on mobile apps available for download in the Apple App Store and Google Play Store, respectively. As described further below, Apple’s new account deletion requirement will apply to all mobile app submissions to the Apple App Store beginning January 31, 2022. Similarly, Google’s new Data Safety section will launch in February 2022, and app developers will be required to submit to the Google Play Store Data Safety forms and P

Advertisement
If you’re considering migrating from DataStax Enterprise (DSE) to open source Apache Cassandra®, our comprehensive guide is tailored for architects, engineers, and IT directors. Whether you’re motivated by cost savings, avoiding vendor lock-in, or embracing the vibrant open-source community, Apache Cassandra offers robust value. Transition seamlessly to Instaclustr Managed Cassandra with our expert insights, ensuring zero downtime during migration.

Schneier on Security
NOVEMBER 8, 2021
We’ve now had an (unsuccessful) assassination attempt by explosive-laden drones.

Dark Reading
NOVEMBER 8, 2021
UL’s SafeCyber will allow organizations to manage cybersecurity governance and processes as well as speed up time spent on firmware development.

OpenText Information Management
NOVEMBER 8, 2021
Many countries, including the UAE, Saudi Arabia and China, have launched ambitious ‘Vision’ programs aimed at dramatic societal and economic transformation. In each case, the national government views digital transformation as a major part of its strategy. While there have been notable successes, there is still a long way to go before these visions are … The post Building on a vision with focus appeared first on OpenText Blogs.

Dark Reading
NOVEMBER 8, 2021
Global business momentum and technical advancements position the Arctic Wolf platform as a category-defining Security Operations solution

Advertisement
Are you trying to decide which entity resolution capabilities you need? It can be confusing to determine which features are most important for your project. And sometimes key features are overlooked. Get the Entity Resolution Evaluation Checklist to make sure you’ve thought of everything to make your project a success! The list was created by Senzing’s team of leading entity resolution experts, based on their real-world experience.

Threatpost
NOVEMBER 8, 2021
Q3 DDoS attacks topped thousands daily, with more growth expected.

Dark Reading
NOVEMBER 8, 2021
Yaroslav Vasinskyi is one of seven individuals believed to be responsible for deploying REvil ransomware in attacks against 5,000 organizations.

HID Global
NOVEMBER 8, 2021
The Importance of Visitor Pre-Registration: 3 Tips to Get Your Organization on Board. kkim. Mon, 11/08/2021 - 13:16.
Let's personalize your content