Back to the Future: Notorious AlphaBay Market Reboots
Data Breach Today
AUGUST 12, 2021
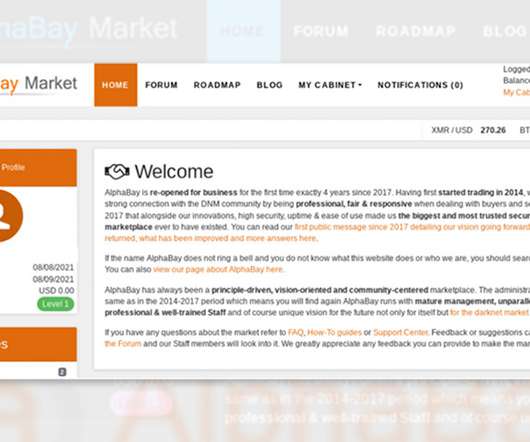
Darknet Market Only Accepts Monero, Promotes Malware and Botnets, Bans Ransomware The notorious AlphaBay darknet marketplace appears to be getting rebooted by "DeSnake," who claims to have been the security administrator for the previous iteration, which law enforcement officials took down in 2017. Whether buyers and sellers will trust it, or the site will survive any takedown efforts, remains to be seen.






































Let's personalize your content