Widespread Internet Outages: Fastly Reports Problem Fixed
Data Breach Today
JUNE 8, 2021
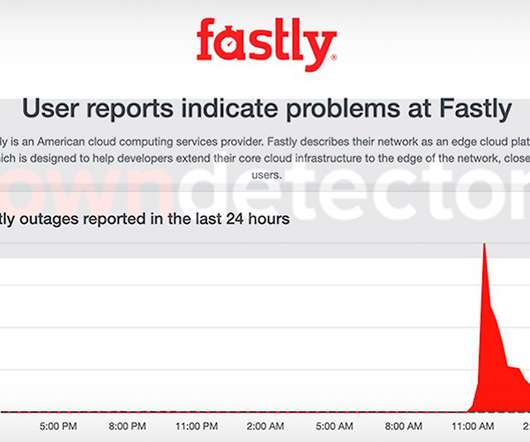
Access to Amazon, Google, Twitter and Others Disrupted by Content Delivery Network Amazon, Google, Spotify and Twitter were among the sites that were unreachable Tuesday morning due to a configuration error at widely used content delivery network Fastly, which said the problem was resolved after about an hour, after which the disruptions would begin to abate.









































Let's personalize your content