FluBot Spyware Spreads Across Europe
Data Breach Today
APRIL 28, 2021
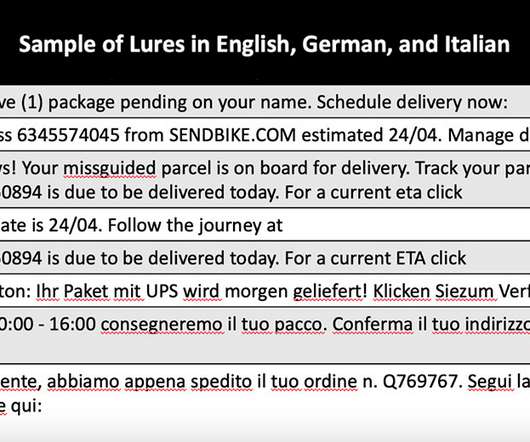
Proofpoint: Malware's Operators Rebound After Arrests FluBot Android spyware is once again spreading throughout Europe following a temporary dip in activity in March after police arrested four suspects allegedly involved in the campaign, according to researchers at Proofpoint.






































Let's personalize your content