Phishing Kit Can Change Lures and Text
Data Breach Today
JANUARY 29, 2021
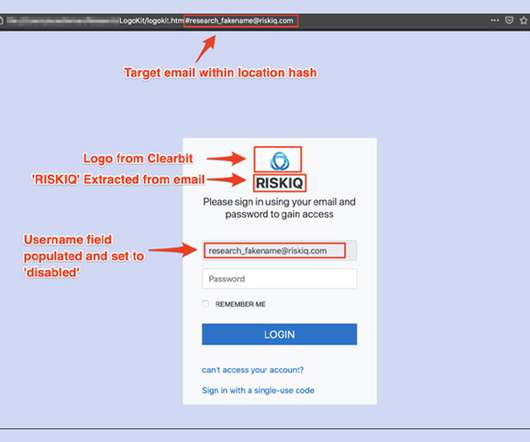
Researchers: 'LogoKit' Found on 700 Domains Researchers at the security firm RiskIQ have discovered a phishing kit they call "LogoKit" that fraudsters can use to easily change lures, logos and text in real time to help trick victims into opening up messages and clicking on malicious links.




































Let's personalize your content