Lazarus Group Targeted COVID-19 Research
Data Breach Today
DECEMBER 24, 2020
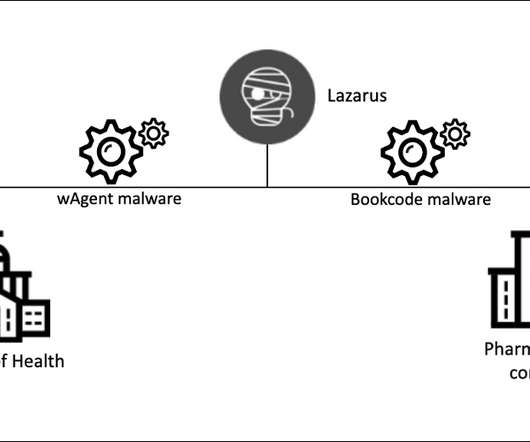
Kaspersky: North Korean APT Group Used Malware in Attempt to Steal Information The Lazarus Group, a North Korean advanced persistent threat gang, apparently recently targeted a national ministry of health and a drug manufacturer involved in developing a COVID-19 vaccine in an attempt to steal information, according to the security firm Kaspersky.





























Let's personalize your content