VMware Flaw a Vector in SolarWinds Breach?
Krebs on Security
DECEMBER 18, 2020
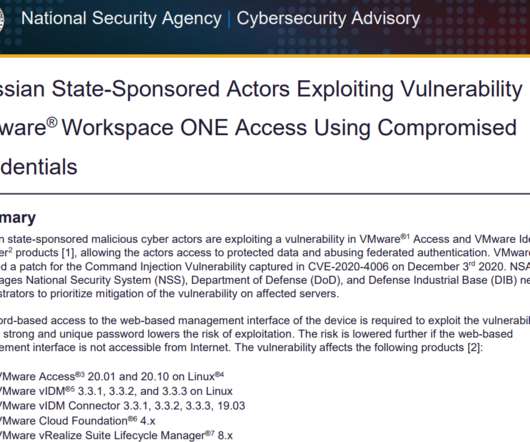
U.S. government cybersecurity agencies warned this week that the attackers behind the widespread hacking spree stemming from the compromise at network software firm SolarWinds used weaknesses in other, non-SolarWinds products to attack high-value targets. According to sources, among those was a flaw in software virtualization platform VMware , which the U.S.








































Let's personalize your content