'Return to Office' Phishing Emails Aim to Steal Credentials
Data Breach Today
NOVEMBER 30, 2020
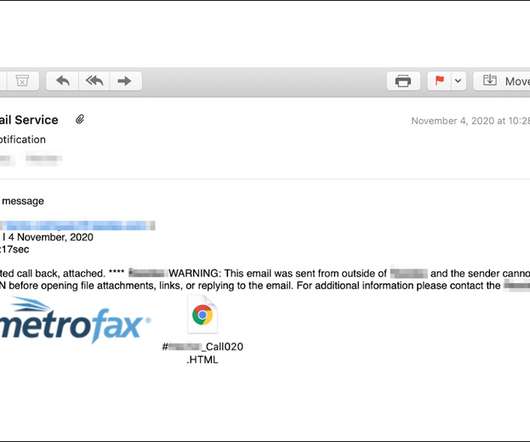
Researchers: Employees Lured With Messages About Shift to Workplace Researchers at Abnormal Security have uncovered a credential-stealing phishing campaign that spoofs internal company memos concerning returning to the office.








































Let's personalize your content