Chinese Hackers Exploit Zerologon Flaw for Cyberespionage
Data Breach Today
NOVEMBER 19, 2020
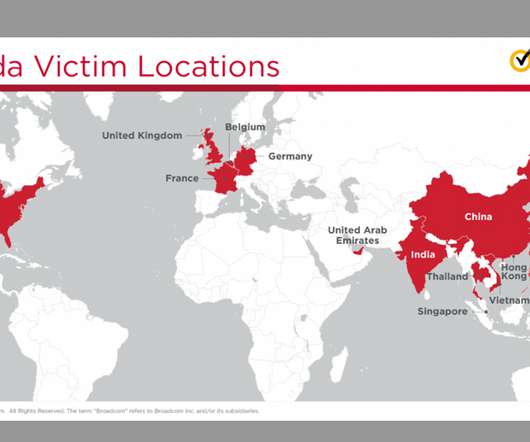
Researchers: 'Cicada' Campaign Targeting Japanese Companies The Chinese hacking group "Cicada" is exploiting the critical Zerologon vulnerability in Windows Server as part of a cyberespionage campaign that's mainly targeting Japanese companies' locations around the world, according to the security firm Symantec.






































Let's personalize your content