Ransomware Danger: Russian-Speaking Gang Targets Russians
Data Breach Today
SEPTEMBER 23, 2020
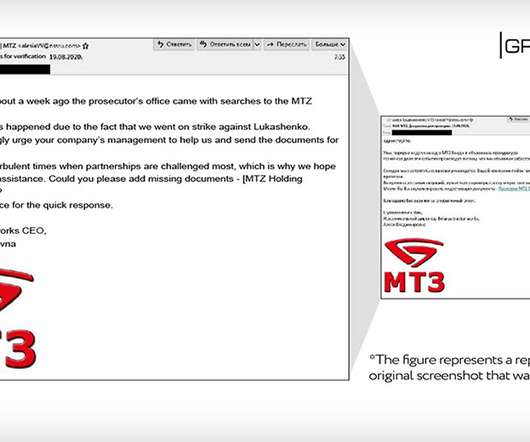
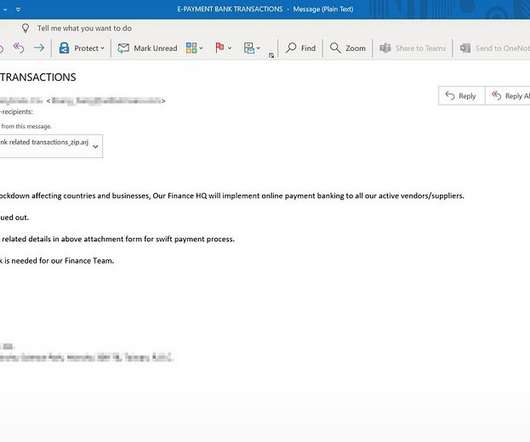
Cybercrime Reminder: Russians Who Target Other Russians Play With Fire Russian criminals operating online who want to stay out of jail need only to follow a few simple rules, the primary one being: Never target Russians. So it's surprising that security researchers have uncovered a new ransomware-wielding gang of Russian speakers that includes Russian victims on its hit list.





































Let's personalize your content