Hackers Use Cloud Monitoring Tool to Install Cryptominers
Data Breach Today
SEPTEMBER 10, 2020
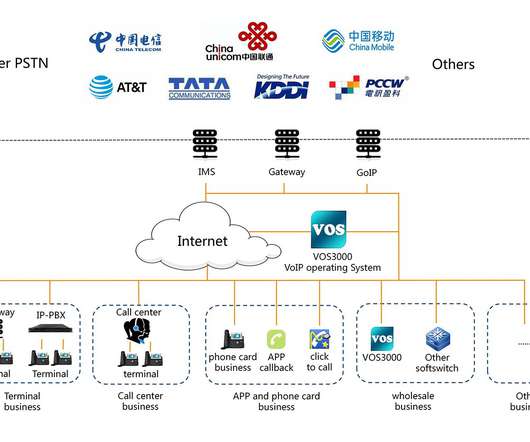
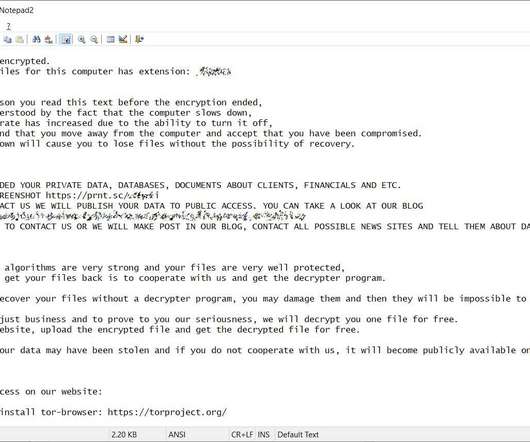
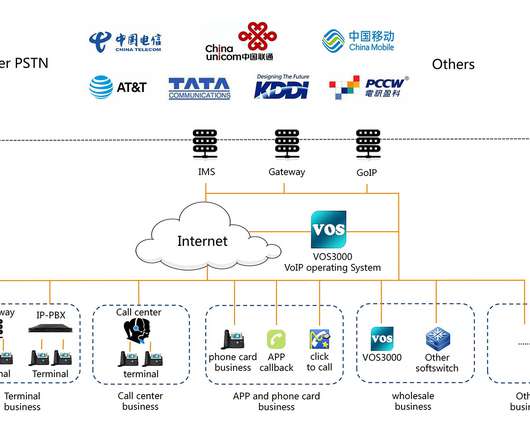
Reports: TeamTNT Using Weave Scope Tool to Target Cloud Platforms TeamTNT, a recently uncovered hacking group, is weaponizing Weave Scope, a legitimate cloud monitoring tool, to help install cryptominers in cloud environments, according to reports from Intezer and Microsoft.







































Let's personalize your content