BEC Scam Losses Surge as the Number of Attacks Diminish
Data Breach Today
SEPTEMBER 7, 2020
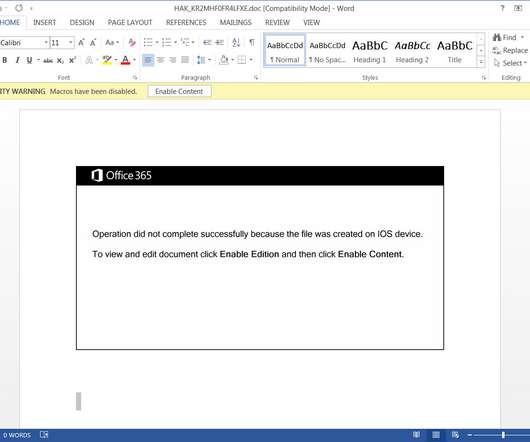
Cosmic Lynx the First Russian Gang to Enter the BEC Game The average amount stolen in a business email compromise (BEC) scam increased 48% during the second quarter of 2020, however, this transpired as the number of attacks decreased during that period, reports the Anti-Phishing Working Group.





























Let's personalize your content