Here’s Why Credit Card Fraud is Still a Thing
Krebs on Security
JULY 29, 2020
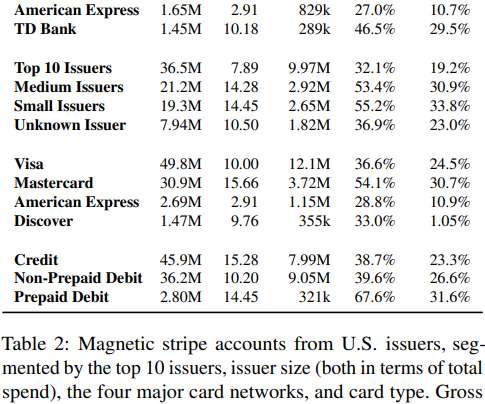
Most of the civilized world years ago shifted to requiring computer chips in payment cards that make it far more expensive and difficult for thieves to clone and use them for fraud. One notable exception is the United States, which is still lurching toward this goal. Here’s a look at the havoc that lag has wrought, as seen through the purchasing patterns at one of the underground’s biggest stolen card shops that was hacked last year.






































Let's personalize your content