Studying an 'Invisible God' Hacker: Could You Stop 'Fxmsp'?
Data Breach Today
JULY 2, 2020
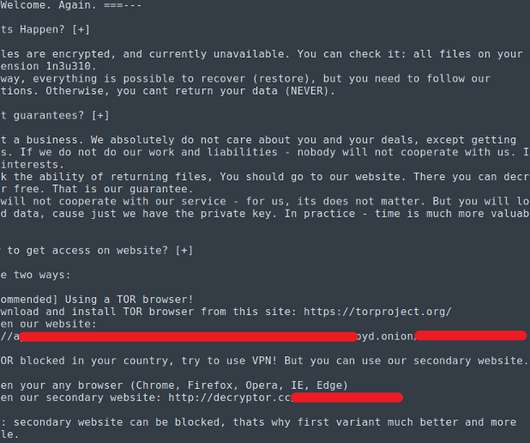
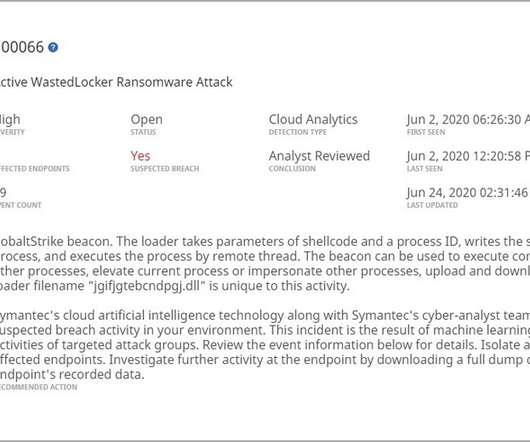
Successful Hacking Operation Often Relied on Simple, Easy-to-Block Tactics Could your organization withstand an attack by the master hacking operation known as "Fxmsp"? Hollywood loves to portray hackers as having ninja-like skills. But Fxmsp often favored the simplest tools for the job, because they so often worked. Defenders: Take note.




































Let's personalize your content