Botnet Watch: Anubis Mobile Malware Gets New Features
Data Breach Today
MAY 11, 2020
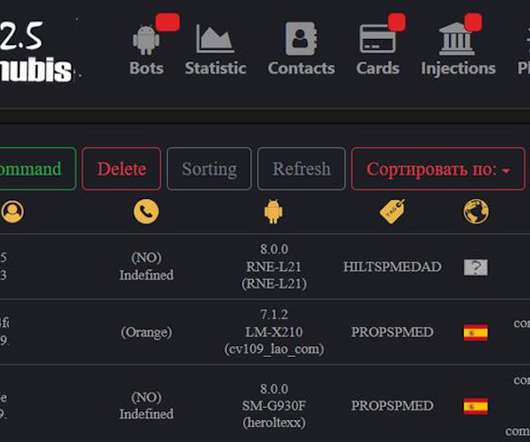
Powerful Platform Can Spot If Victim Is Looking at the Screen Anubis, one of the most potent Android botnets, apparently is getting a refresh a year after its source code was leaked, security researchers say. The changes could help fraudsters more closely monitor activity on hacked devices.









































Let's personalize your content