The Evolution of Cloud Governance
Data Breach Today
MARCH 6, 2020
Expanse CTO Matt Kraning on Meeting New Demands for Cloud Security The good news is: Organizations are embracing the cloud, and that's a boon to velocity and digital transformation. The bad news: Visibility and governance take a huge hit. Matt Kraning, CTO and co-founder of Expanse, discusses this challenge and how to improve cloud governance.











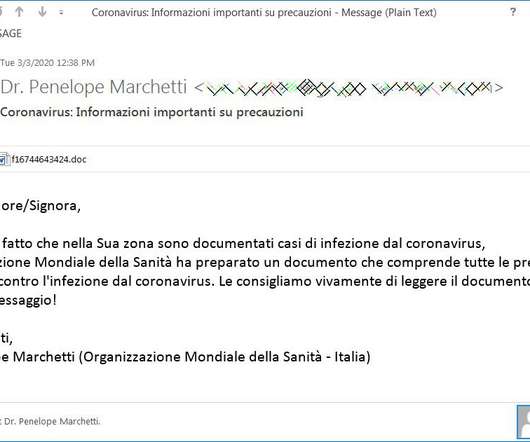































Let's personalize your content