DDoS: An Underestimated Threat
Dark Reading
NOVEMBER 26, 2019
Distributed denial-of-service (DDoS) attacks have become more common, more powerful, and more useful to attackers. Here's how to fight back.

Dark Reading
NOVEMBER 26, 2019
Distributed denial-of-service (DDoS) attacks have become more common, more powerful, and more useful to attackers. Here's how to fight back.
Krebs on Security
NOVEMBER 26, 2019
On Nov. 23, one of the cybercrime underground’s largest bazaars for buying and selling stolen payment card data announced the immediate availability of some four million freshly-hacked debit and credit cards. KrebsOnSecurity has learned this latest batch of cards was siphoned from four different compromised restaurant chains that are most prevalent across the midwest and eastern United States.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Data Breach Today
NOVEMBER 26, 2019
Company Acquired RSA as One Component of Its Purchase of EMC in 2016 Dell Technologies is considering the possible sale of its RSA security division, hoping such a deal could be worth $1 billion, according to Bloomberg, which cites "people familiar with the matter.

IT Governance
NOVEMBER 26, 2019
T-Mobile has confirmed that its systems have been hacked, with cyber criminals stealing the personal data of more than one million US customers. According to the organisation, customer names, addresses, phone numbers, rate plans and plan features were all exposed. Other sensitive information such as passwords and financial information weren’t affected.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.

Data Breach Today
NOVEMBER 26, 2019
Government Auditor Highlights Third-Party Risks The Australian government's digital health records program manages risk and privacy relatively well, according to a new audit, but there's room for improvement in third-party risk management and emergency access to sensitive health records.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

Data Breach Today
NOVEMBER 26, 2019
Election hacking is not just a US issue; it's a hot topic for every global democracy. And Joseph Carson of Thycotic is concerned that too many people are focused on the wrong elements of this topic. He analyzes the specific hacking techniques that demand attention.
Security Affairs
NOVEMBER 26, 2019
Some third-party apps quietly scraped personal information from people’s accounts from Twitter and Facebook, the social media companies claim. Facebook and Twitter revealed that some third-party apps quietly scraped personal information from people’s accounts without their consent. According to the company, the cause of behavior that violates their policies is a couple of “malicious” software development kits (SDKs) used by the third-party iOS and Android apps.

Data Breach Today
NOVEMBER 26, 2019
Three Key Areas That Need Clarification With the California Consumer Privacy Act set to go into effect Jan. 1, 2020, companies are making last-minute compliance preparations. But these preparations are challenging because regulations to carry out the law are still pending and ambiguities remain. Here's a look at three issues.
Security Affairs
NOVEMBER 26, 2019
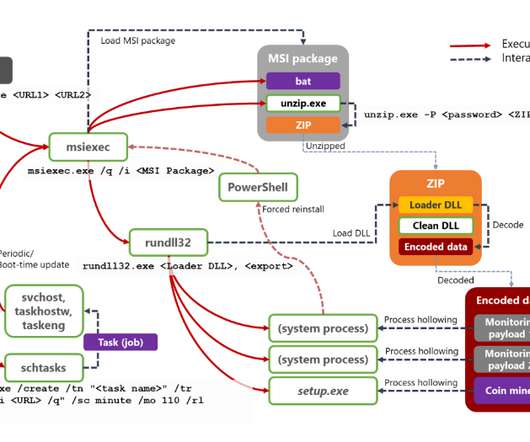
Microsoft revealed that the new Dexphot cryptocurrency miner has already infected more than 80,000 computers worldwide. Security experts at Microsoft analyzed a new strain of cryptocurrency miner tracked as Dexphot that has been active since at least October 2018. The malicious code abuse of the resources of the infected machine to mine cryptocurrency , according to the experts it has already infected 80,000 computers worldwide.

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.

Adam Levin
NOVEMBER 26, 2019
One terabyte of data belonging to a major hotel booking platform was found leaked online. A huge trove of customer data belonging to Gekko Group was found online in an unsecured format. The data contained a wide array of records, including full names, credit card details, client login information, email addresses, home addresses and hotel reservations.
Security Affairs
NOVEMBER 26, 2019
Researchers at SEC Consult Vulnerability Lab discovered multiple issues in several security products from Fortinet, including hardcoded key and encryption for communications. Security researchers from SEC Consult Vulnerability Lab discovered that multiple Fortinet products use a weak encryption cipher (“XOR” with a static key) and cryptographic keys to communicate with the FortiGuard Web Filter, AntiSpam and AntiVirus cloud services.
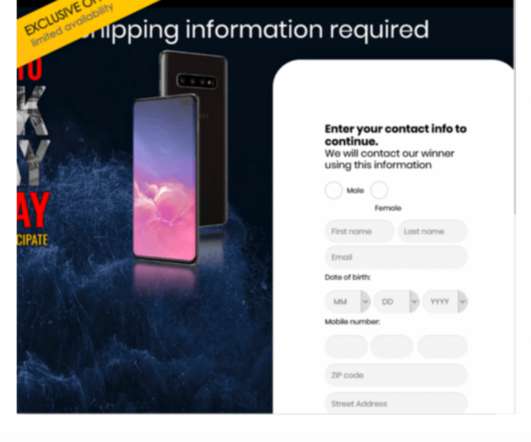
Threatpost
NOVEMBER 26, 2019
Cybercriminals are tapping in on Black Friday and Cyber Monday shoppers with an array of scams and malware - including domain impersonation, social media giveaway scams, and a malicious Chrome extension.

Thales Cloud Protection & Licensing
NOVEMBER 26, 2019
Originally published in Security Magazine on November 20, 2019. With the holidays approaching, many of us are thinking about taking time off from work to be with friends and family, as well all the last minute shopping that needs to be done. The sad truth is that cyber criminals do not take vacations and may be looking at the holidays as yet another opportunity to steal and monetize consumer data.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.
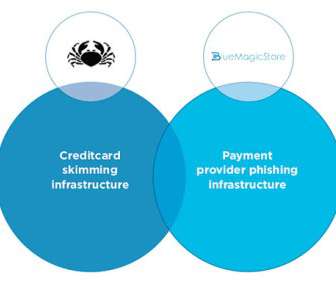
Security Affairs
NOVEMBER 26, 2019
A group under the Magecart umbrella adopted a new tactic that leverages on MiTM and phishing attacks to target sites using external payment processors. Security experts at RiskIQ continue to monitor activities of several Magecart groups, recently they spotted a new crew, tracked as Full ( z) House, that leverages phishing and web skimming for its attacks.

AIIM
NOVEMBER 26, 2019
How much does Records Management training cost? In a way, it’s a bit like asking, “How much does dinner cost?” So much of the answer depends on what you want. The cost of dinner could run anywhere from a couple of bucks for those pursuing the dollar menu at their favorite fast food joint, to something like “ The Posh Pie ” at the Lord Dudley Hotel in Sydney, Australia, which comes with a hefty $12,000 price tag.

Security Affairs
NOVEMBER 26, 2019
Aircraft warning lights, an essential component of the aviation infrastructure, but they pose a serious risk if controlled by hackers. The independent researcher Amitay Dan discovered that control panels for aircraft warning lights were exposed to the Internet, potentially allowing attackers to control them with unpredictable and catastrophic consequences.

Dark Reading
NOVEMBER 26, 2019
Give your organization's leadership an impactful, out-of-office experience so they know what's at stake with their budgeting decisions.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.
Security Affairs
NOVEMBER 26, 2019
A Czech intelligence report states that Russian and Chinese cyberspies carried out several attacks against the country during 2018. The Czech intelligence agency ‘Security Information Service (BIS)’ published a report on the activities related to 2018 that claims that Russian and Chinese cyberspies carried out several attacks against the country.

Micro Focus
NOVEMBER 26, 2019
#COBOL60 recap I’m pretty sure that you’ll have heard the news that COBOL turned 60 in September 2019 but if this somehow passed you by, please visit our dedicated #COBOL60 page to read the press, download the whitepaper, enjoy the webinar recording and generally find out more. COBOL is arguably one of the most pervasive. View Article.
Security Affairs
NOVEMBER 26, 2019
Kaspersky has fixed several flaws affecting the web protection features implemented in some of its security products. Kaspersky has addressed several vulnerabilities in the web protection features implemented in its antivirus solutions, including Internet Security, Total Security, Free Anti-Virus , Security Cloud, and Small Office Security products.

Dark Reading
NOVEMBER 26, 2019
Gamification is becoming popular as companies look for new ways to keep employees from being their largest vulnerability.

Advertisement
If you’re considering migrating from DataStax Enterprise (DSE) to open source Apache Cassandra®, our comprehensive guide is tailored for architects, engineers, and IT directors. Whether you’re motivated by cost savings, avoiding vendor lock-in, or embracing the vibrant open-source community, Apache Cassandra offers robust value. Transition seamlessly to Instaclustr Managed Cassandra with our expert insights, ensuring zero downtime during migration.

Hunton Privacy
NOVEMBER 26, 2019
On November 26, 2019, the European Data Protection Supervisor’s office (“EDPS”) and the European Parliament announced that Wojciech Wiewiórowski , currently Assistant Supervisor and acting replacement for the European Data Protection Supervisor Giovanni Buttarelli, will officially be the new European Data Protection Supervisor for the new term of office.

Threatpost
NOVEMBER 26, 2019
He and co-conspirators stole 50 gigs of music and leaked some of it onto the internet.

The Schedule
NOVEMBER 26, 2019
In his presidential address at the 1965 SAA annual meeting, W. Kaye Lamb spoke about “ The Changing Role of the Archivist.” He spoke at length about the importance of good records management, including this praise: “Our debt to the records managers is very great, in at least two respects. In the first place, it is they who are bringing order out of chaos in the handling of official papers and who have made possible the systematic retirement of files from which archival collect

Threatpost
NOVEMBER 26, 2019
Convincing employees to take security seriously takes more than awareness campaigns.

Advertisement
Are you trying to decide which entity resolution capabilities you need? It can be confusing to determine which features are most important for your project. And sometimes key features are overlooked. Get the Entity Resolution Evaluation Checklist to make sure you’ve thought of everything to make your project a success! The list was created by Senzing’s team of leading entity resolution experts, based on their real-world experience.

Robert's Db2
NOVEMBER 26, 2019
Not long ago, a very experienced Db2 for z/OS person contacted me with some questions about the CICS-Db2 interface. He mentioned that he did this because he was having trouble finding the information he was seeking in the product documentation. I provided this person with answers to his questions, and then thought to myself, "If a veteran Db2 for z/OS technical professional was challenged in getting a clear picture of the CICS-Db2 interface, perhaps other people are in the same boat.

HL Chronicle of Data Protection
NOVEMBER 26, 2019
Hogan Lovells has published a study evaluating the ongoing legislative proposal for a new ePrivacy Regulation, a law aimed at updating the current ePrivacy framework in the EU. After nearly three years of debates and negotiations, the European Union is nowhere near agreeing on a position for how to achieve the right balance between the need for technological innovation, public security, and the protection of privacy in the context of the digital economy.

Threatpost
NOVEMBER 26, 2019
This new skimming/phishing hybrid threat tactic means that even stores that send customers to external payment processors are vulnerable.
Let's personalize your content