Insurer CNA Disconnects Systems After 'Cybersecurity Attack'
Data Breach Today
MARCH 24, 2021
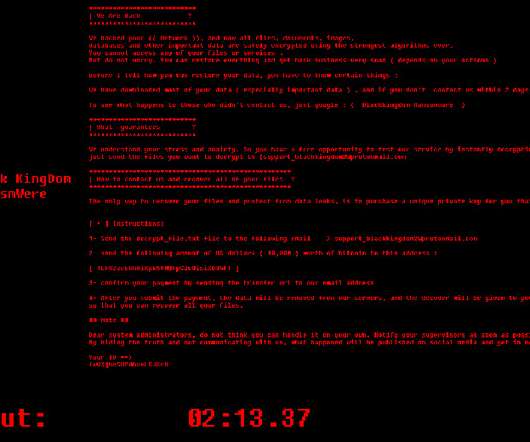
Investigation Continues; Law Enforcement Notified Insurance provider CNA reported Tuesday it was victimized over the weekend by a "cybersecurity attack" that caused a network disruption and impacted certain systems, including corporate email.







































Let's personalize your content