'FreakOut' Botnet Targets Unpatched Linux Systems
Data Breach Today
JANUARY 20, 2021
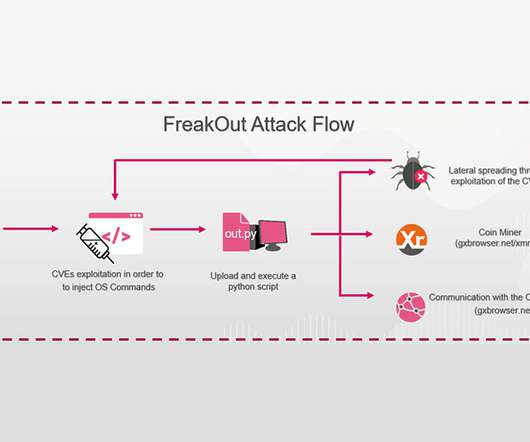
Researchers Says Malicious Network Could Be Used to Launch DDoS Attacks Researchers at Check Point Research are tracking a new botnet dubbed "FreakOut" that's targeting vulnerabilities in Linux systems. The malware is creating a malicious network that has the potential to launch DDoS attacks.





































Let's personalize your content