Nation-State Hackers Using COVID-19 Fears to Spread Malware
Data Breach Today
MARCH 16, 2020
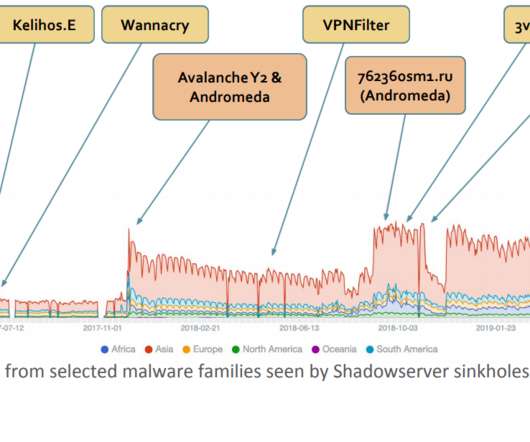
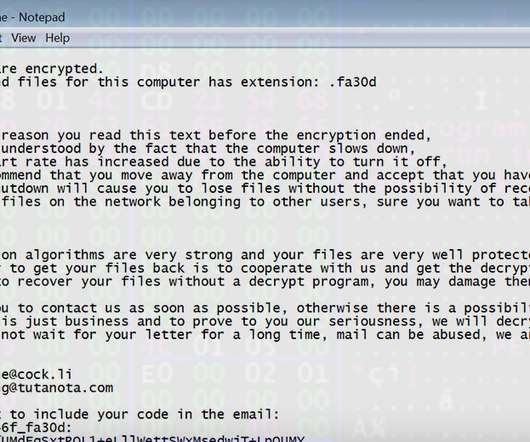
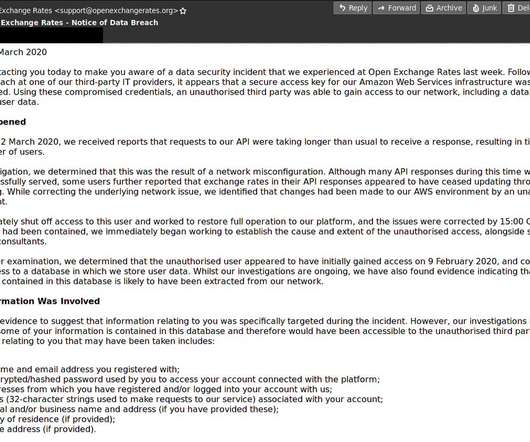
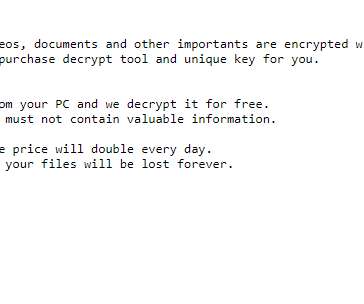
Researchers Find Healthcare Crisis Used As a Lure for Phishing Emails Nation-state hackers as well as cybercriminals are now attempting to use phishing emails with themes tied to the global COVID-19 pandemic to spread malware, according to recent security reports.




































Let's personalize your content